Kerala Plus Two Computer Science Previous Year Question Paper March 2018 with Answers
| Board | SCERT |
| Class | Plus Two |
| Subject | Computer Science |
| Category | Plus Two Previous Year Question Papers |
Time: 2 Hours
Cool off time : 15 Minutes
General Instructions to candidates
- There is a ‘cool off time’ of 15 minutes in addition to the writing time of 2 hrs.
- Your are not allowed to write your answers nor to discuss anything with others during the ‘cool off time’.
- Use the ‘cool off time’ to get familiar with the questions and to plan your answers.
- Read questions carefully before you answering.
- All questions are compulsory and only internal choice is allowed.
- When you select a question, all the sub-questions must be answered from the same question itself.
- Calculations, figures and graphs should be shown in the answer sheet itself.
- Malayalam version of the questions is also provided.
- Give equations wherever necessary.
- Electronic devices except non-programmable calculators are not allowed in the Examination Hall.
Part – A
Answer all questions from 1 to 5. Each carries 1 score. (5 × 1 = 5)
Question 1.
Showing only the essential features and hiding complexities from Outside World refers to ________
Answer:
Abstraction
Question 2.
Name the data structure where memory allocation is done only at the time of execution.
Answer:
Linked List
Question 3.
The space between content and cell border in a table can be changed using ________ attribute.
Answer:
cell padding
Question 4.
What is the expansion of LAMP?
Answer:
Linux Apache MySQL PHP
Question 5.
New domain names are checked in the database of ________ before approving registration.
Answer:
www.whois.net
Answer any nine questions from 6 to 16. (Scores: 9 × 2 = 18)
Question 6.
Identify the correct errors in the following code fragment:
Struct
{
int regno;
char name [20];
float mark = 100;
};
Answer:
The errors are given below:
1. Instead of Struct write struct with a tag name as follows
struct student
2. The variable mark is a float variable hence it must be initialized with a float value as follows
float mark=100.0;
The correct code is as follows
struct student
{
int regno;
charname[20];
float mark=100.0;
};
Question 7.
What is the difference between static and dynamic memory allocation?
Answer:
We know that memory is classified into two primary and secondary. Just like that data structures are classified as static and dynamic. Static data structure is associated with primary memory. The needed memory is allocated before the execution of the program and it is fixed throughout the execution. The array is an example of this. In a Dynamic data structure, memory is allocated during execution. A linked list is an example of this.
Question 8.
Write an algorithm to add a new item into a stack.
Answer:
Push operation
the algorithm is given below:
Step 1: If top=N. Then print “OVERFLOW” and return
Step 2: Set top = top+1
Step 3: Set Stack[top]=item
Step 4: stop
Question 9.
Write the HTML code fragment to insert an image “Profile.jpg” aligned in center of a webpage.
Answer:
<center>
<img src=”Profile.jpg” width=100 height=100>
</center>
Question 10.
The following code in HTML will call the Show Message () in Java Script.
<input type = “button” value = ‘show’ onClick=”ShowMessage();”>
Modify the code to call the ShowMessage() when”
(a) User moves the mouse over the button
(b) User presses any key on the keyboard
Answer:
(a) <input type=”button” value=”show” onMouseEnter=”ShowMessage()”>
(b) <input type=”button” value=”show” onKeyDown=”ShowMessage()”>
Question 11.
Consider two strings “Education is the most powerful weapon” and “you can use to change the world”.
Write JavaScript code to:
(a) Store these strings in two variables
(b) Combine the two string variables.
Answer:
<html>
<head>
<Script Language=”JavaScript”>
function combine()
{
var str1, str2, str3;
str1=”Education is the most powerful weapon”;
alert(“First string is-”+str1);
str2=”You can use to change the world”;
alert(“Second string is-”+str2);
str3=str1+”.”+str2;
alert(“The combined string is-“+str3);
}
</Script>
</head>
<body>
<center>
<form name=”frm”>
<input type=”button” value=”Combine two strings” onClick=”combine()”>
</form>
</center>
</body>
</html>
Question 12.
What is the primary key? What is the significance of the primary key in a relation?
Answer:
Primary key – It is a set of one or more attributes used to uniquely identify a row. It does not allow to enter same values in a column.
Question 13.
Consider the given table SPORTS and write relational expressions for the following questions:
| P/D | Name | Goals | Games |
| 1 | Maradona | 90 | 85 |
| 2 | Carlos | 70 | 68 |
| 3 | Messi | 80 | 49 |
| 4 | Robert | 75 | 60 |
(a) Select the name of all players
(b) Select Name and Goals scored by players who have scored more than 70 goals.
Answer:
(a) p Name (SPORTS)
(b) p Name, Goals (s Goals > 70 (SPORTS))
Question 14.
Name the global variables used for passing data using HTTP GET and POST requests.
Answer:
GET:DatapassedusingtheHTTPGETmethodGET:DatapassedusingtheHTTPGETmethod_POST: Data passed using the HTTP POST method.
Question 15.
What is cyberspace? How cyberspace has influenced our life?
Answer:
Nowadays telephone systems and computer System are integrated and create a virtual(unreal) environment. This is called cyberspace. The result of this integration is that tremendous speed and it is very cheap. The various departments of Govt, are providing speed, reliable and convenient online service hence increase productivity. Online shopping, Online banking, Online debate, Online Auction, etc. are the various services offered by the Internet.
Question 16.
What Is Artificial Neural Networks?
Answer:
Artificial Neural Networks (ANN): The brain is a complex, nonlinear, and parallel computer with the ability to perform tasks such as recognise pattern, perception and motor control. ANN is the method of simulate biological neural systems to learn, memorise and generalize like human beings. A human brain cortex consists of 10-500 billion neurons with 60 trillion synapses (a synapse is a structure that permits a neuron to pass electrical)
Answer any nine questions from 17 to 27. (Scores: 9 × 3 = 27)
Question 17.
Read the following code fragment;
int a [ ] = {5, 10, 15, 20, 25};
int *p = a;
Predict the output of the following statements:
(a) count<<*p;
(b) count<<*p+1;
(c) count<<*(p+1);
Answer:
(a) 5 (i.e. the content of the starting address)
(b) 6 (i.e. the content of the starting address, 5+1=6)
(c) 10 (i.e. the content of, the starting address+1. The second element)
Question 18.
What is the object-oriented programming paradigm? Give any two advantages.
Answer:
There are many drawbacks in Procedural Programming Paradigm, OOP eliminates these problems. It wraps data and functions into a single unit. Such units are called objects.
Advantages of using OOP are
- OOP allows modularity(divide the large programs into smaller ones)
- It is good for defining abstract data types.
- It allows data abstraction. That is it hides or protects data.
- It allows code reusability
- Real-life entities can be easily created
- It supports creating new data types.
Question 19.
What is the data structure? How are they classified?
Answer:
Data Structure: It is a particular way of organizing similar or dissimilar logically related data items into a single unit.
Classification of data structures: Classified as simple(Array and structure) and compound. Compound(mixture) data structure is further classified as linear and nonlinear. A data structure is said to be linear if its elements form a sequence(it needs contiguous memory location) otherwise it is called a non-linear data structure needs random memory)
The examples of Linear data structures are stack, queue, and linked list.
Question 20.
List and explain any three attributes of the BODY tag in HTML.
Answer:
Attributes of the Body tag.
Bgcolor: Used to set the background colour.
Text: This specifies the colour of the text content in the page.
Background: It sets an image as the background for the document body.
Question 21.
Identify suitable JavaScript data types for the following:
(a) “supercomputer”
(b) “true”
(c) 67.5
Answer:
(a) String
(b) String/Boolean
(c) Number
Question 22.
What is Responsive Web Design? What is its significance in modem computing devices?
Answer:
The home page is displayed differently according to the screen size of the browser window(different screen sized devices-mobile phone, palm top, tablet, laptop, and desktop) we used. The website is designed dynamically(flexibly) that suit the screen size of a different device introduced by Ethan Marcotte. Before this, companies have to design different websites for different screen sized devices. By responsive web design, companies have to design only one website that suitably displayed according to the screen size of the devices.
Question 23.
Define the following terms:
(a) Relation
(b) Candidate key
(c) Tuples and attributes
Answer:
Relation – Tables are called relation
Candidate key – It is used to uniquely identify the row.
Tuple – Rows are called tuples
Attributes – Columns are called attributes.
Question 24.
Write short notes on any three data types in SQL.
Answer:
Data Types
- Char – It is used to store fixed number of characters. It is declared as char(size).
- Varchar – It is used to store characters but it uses only enough memory.
- Dec or Decimal – It is used to store numbers with decimal pdint. It is declared as Dec (size, scale). We can store a total of size number of digits.
- Intorlnteger – It is used to store numbers without decimal point. It is declared as int. It has no argument. Eg: age int.
- Smallint- Used to store small integers.
- Date – It is used to store date. The format is yyyy-mm-dd. Eg:‘1977-05-28’.
- Time – It is used to store time. The format is HH:MM:SS. Eg: ‘22:32:45’.
Question 25.
What is the difference between echo and print in PHP?
Answer:
echo and print are used to display all types of data but echo is used to produce multiple outputs.
Parenthesis is optional.
eg: echo “ first output”, “second output”;
or
echo (“ first output”, “second output”);
print “only one output”;
or
print (“only one output”);
Question 26.
Define the following cybercrimes:
(a) Identify Theft
(b) Harassment
(c) Impersonation and cheating
Answer:
a) Identity theft: The various information such as personal details(name, Date of Birth, Address, Phone number etc) , Credit / Debit Card detai!s(Card number, PIN, Expiry Date, CW, etc), Bank details, etc. are the-identity of a person. Stealing these information by acting as the authorized person without the permission of a person is called Identity theft. The misuse of this information is a punishable offence.
b) Harassment: Commenting badly about a particular person’s gender, color, race, religion, nationality, in Social Media is considered as harassment. This is done with the help of the Internet is called Cyberstalking (Nuisance). This is a kind of torturing and it may lead to spoiling friendship, career, self-image, and confidence. Sometimes may lead to a big tragedy of a whole family or a group of persons.
c) Impersonation and cheating: Fake accounts are created in Social media and act as the original one for the purpose of cheating or misleading others.
Eg: Fake accounts in Social Medias (Facebook, Twitter, etc), fake SMS, fake emails, etc.
Question 27.
Briefly explain different types of cloud services.
Answer:
It is an emerging computing technology. Herewith the use of the Internet and central remote servers to maintain data and applications. Example of this is Email service, Office Software (word processor, spreadsheets, presentations, data base etc), graphic software etc. The information is placed in a central remote server just like clouds in the sky hence the name cloud computing.
Cloud Service Models (3 major services)
1. Software as a Service (SaaS): A SaaS provider company provides more services on demand such as they allow to access both resources and applications. Examples are Google Docs, Adobe creative cloud, Microsoft Office 365, Facebook.com etc.
2. Platform as a Service (PaaS): A PaaS provider company provides subscribers access to the components that they require to develop and operate applications over the Internet.
Example: LAMP platform (Linux, Apache Server, MySQL and PHP), ASP.NET, PHP and Python, Google’s App Engine, Microsoft Azure, Force.com, etc.
3. Infrastructure as a Service (IaaS): It provides basic storage devices and computing capabilities as standardized services over the network.
Example: Amazon Web Services, Joyent, AT&T, GoGrid etc.
Answer any two questions from 28 to 30. (5 score each) (Scores: 2 × 5 = 10)
Question 28.
Write SQL queries based on the table STUDENT given below:
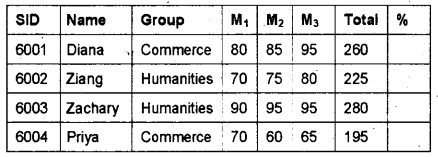
- Add a new field percentage to the table.
- Update percentage of all students (Percentage = Total /3)
- Find the average column total from students in the commerce batch.
- Delete all students in the Humanities batch.
- Find the number of students whose percentage is greater than 90.
Answer:
- ALTER TABLE STUDENT ADD Percentage decimal (5, 2);
- UPDATE STUDENT SET Percentage=Total/3;
- SELECT AVG(Total) FROM STUDENT WHERE Group=’Commerce’;
- DELETE FROM STUDENT WHERE Group=’Humanities’;
- SELECT COUNT(*) FROM STUDENT WHERE Percentage >90;
Question 29.
(a) Name the different types of communication on the web and explain briefly. (Scores: 3)
(b) What is a web server? (Scores: 2)
Answer:
(a) Client to web server communication
This communication is carried out between the client to the webserver (shopping site). The technology used to protect data that are transferred from, client to the webserver is HTTPS (HyperText Transfer Protocol Secure). This encrypts user name, password etc. and sent to the server. HTTPS works using Secure Sockets Layer (SSL) ensures privacy as well as prevents it from unauthorised access (changes) from other websites.
Following are the steps
- Browser requests a web page to the server:
- The server returns its SSL certificate.
- Browser checks the genuinity of the certificate by the authorised certification authority (Eg: Verisign).
- The certificate authority certifies whether it is valid or not.
- If it is valid the browser encrypts the data and transmits. The certificate can be viewed by click on the lock symbol.
Web server to web server communication: This communication is usually carried out between the web server (seller) to another web server (normally a bank). For safe transactions, Digital certificate issued by third-party web sites is used.
A payment gateway is a server (Computer) that acts as a bridge (interface) between the merchant’s server and bank’s server to transfer money.
(b) Webserver
A computer with high storage capacity, high speed and processing capabilities is called a web server. Hence it is a powerful computer with a server operating system and software for providing services like www, e-mail etc. Popular server operating systems are Redhat, OpenSUSE, Debian, Ubuntu, Sun Solaris, Microsoft Windows Server etc.
Question 30.
Identify errors in the following HTML code:
(a) <UL type = “A” start = 5>
(b) <h1><b> web programming </b> </i> </hl>
(c) <img src = ‘Profile.jpg’ size = 50>
(d) <a href = “[email protected]”>
(e) <frameset rows = “50%, 25%, 25%”>
<frame src = “1.html”>
<frame src = “2.html”>
</frameset>
Answer:
(a) <UL> tag has no type and start attribute. It is an Ordered list hence use <OL>
The correct code is <OL type=”A” start=5>
(b) <i> tag is missing
The correct code is <h1> <i><b> web programming</b></i></h1>
(c) <img> tag has no size attribute.
The correct code is
<img src=”Profile.jpg” width=”100″ height=”100″>
(d) missing mailto: while creating an email link
The correct code is
<a href=mailto:”[email protected]”>
(e) Here the browse window is divided into three rows hence one frame is missing.
The correct code is
<frameset rows =”50%, 25%, 25%”>
<frame src=”1 .html”>
<frame src=”2.html”>
<frame src=”3.html”>
</frameset>
