Kerala Plus Two Computer Science Chapter Wise Questions and Answers Chapter 12 ICT and Society
Plus Two Computer Science ICT and Society One Mark Questions and Answers
Question 1.
IPR stands for ______.
Answer:
Intellectual Property Right.
Question 2.
WIPO stands for _____.
Answer:
World Intellectual Property Organisation
Question 3.
______ is the exclusive rights to prevent unauthorized copying of inventions by a Creator from the Unauthorised person or company.
Answer:
Patent
Question 4.
_____ is a unique, simple and memorable sign to promote a brand and hence increase the business and goodwill of a company.
Answer:
Trademark
Question 5.
A product or article is designed so beautifully to attract customers. This type of design is called
Answer:
Industrial Design.
Question 6.
Aranmula Kannadi, Palakkadan Matta, Marayoor Sarkkara, etc are example of _______.
Answer:
Geographical indications.
Question 7.
_____ is the property right that arises automatically when a person creates a new work by his own and by Law it prevents the others from the unauthorized or intentional copying of this without the permission of the creator.
Answer:
Copyright
Question 8.
From the following which is the symbol for copyright.
(a) $
(b) ©
(c) ®
(d) ™
Answer:
(b) ©
Question 9.
From the following which is the symbol for Unregistered trademark.
(a) $
(b) ©
(c) ®
(d) ™
Answer:
(d) ™
Question 10.
From the following which is the symbol for Registered trademark.
(a) $
(b) ©
(c) ®
(d) ™
Answer:
(c) ®
Question 11.
Unauthorized copying or use of Intellectual property rights such as Patents, Copyrights and Trademarks are called ____.
Answer:
Intellectual Property Infringement.
Question 12.
_____ prevents others from the unauthorized or intentional copying or use of Patent without the permission of the creator.
Answer:
Patent Infringement.
Question 13.
______ is the illegal copying, distribution, or use of software.
Answer:
Piracy.
Question 14.
______ prevents others from the unauthorized or intentional copying or use of Trademark without the permission of the creator.
Answer:
Trademark Infringement
Question 15.
_____ prevents others from the unauthorized or intentional copying or use of Copy right without the permission of the creator.
Answer:
Copy right Infringement
Question 16.
______ is a virtual environment created by computer systems connected to the internet
Answer:
Cyberspace
Question 17.
A person committing crimes and illegal activities with the use of computers over Internet. This crime is included as _____ crime.
Answer:
Cybercrime
Question 18.
State True or False.
Cybercrimes can be classified into three categories such as against individual, property, and Government.
Answer:
True
Question 19.
Phishing, hacking, denial of service attacks, etc are ____ crimes.
Answer:
Cyber
Question 20.
Odd one out
(а) Identity theft
(b) Harassment
(c) violation of privacy
(d) credit card fraud
Answer:
(d) credit card fraud, it is a cybercrime against individual others are cyber crimes against property.
Question 21.
Odd one out
(a) Credit card theft
(b) Intellectual property theft
(c) Internet time theft
(d) Dissemination of obscene material
Answer:
(d) Dissemination of obscene material, It is cyber , crime against individual, the others are cyber against property.
Question 22.
Odd one out
(a) cyberterrorism
(b) Attacks against e-Governance websites
(c) Impersonation and cheating
(d) Website defacement
Answer:
(c) Impersonation and cheating, it is cybercrime against individual others are cyber crimes against Government.
Question 23.
IT Act amended in _____.
(a) 2015
(b) 2008
(c) 1900
(d) 1998
Answer:
(b) 2008
Question 24.
IT Act passed in Indian parliament is ____.
Answer:
2000.
Question 25.
The laws to prevent cyber crimes is termed as ____.
Answer:
Cyberlaw
Question 26.
_____ excessive enthusiasm for acquiring knowledge.
Answer:
Infomania
Question 27.
Phishing is an example of ______.
Answer:
Cybercrime.
Question 28.
ICT stands for _______.
(a) Internet and Communication Technology
(b) Information and Computer Technology
(c) Information and Communication Technology
(d) Integrated Communication Technology
Answer:
(c) Information and Communication Technology
Question 29.
Which of the following e-Governance helps citizens for interacting with the Government?
(a) G2E
(b) G2B
(c) G2C
(d) G2G
Answer:
(c) G2C
Question 30.
What are the different types of interactions in e-Governance?
Answer:
G2G, G2E.G2B, G2C.
Question 31.
The unauthorized use of intellectual property rights is termed as
Answer:
Infringement
Question 32.
Expand the term WIPO in connection with IPR.
Answer:
World Intellectual Property Organization.
Question 33.
The exclusive right granted to an invention is called
(a) Trademark
(b) Copy right
(c) Patent
(d) Design
Answer:
(c) Patent
Question 34.
The exclusive right given to a person over the creation of his/her mind for a period of time is called
Answer:
Patent / Intellectual Property Right
Question 35.
What is the name given to the process of using scientific knowledge for analyzing and presenting evidence of cyber related crimes before court?
Answer:
Cyber forensics
Question 36.
Which among the following are considered as violation to privacy?
1. Keeping hidden cameras in private places
2. Publishing private photos of individual in social media without their permission
3. Use of unauthorized software
4. Using simple password
(A) All the above are correct
(B) 1,2 and 3 only
(C) 1 and 4 only
(D) 1 and 2
Answer:
(D) 1 and 2
Plus Two Computer Science ICT and Society Two Mark Questions and Answers
Question 1.
“IPR (Intellectual Property Right) encourages innovation” Justify.
Some people spend lots of money,time body and mental power to create some products such as a classical movie, album, artistic work, discoveries, invention, software, etc. These type of Intellectual properties must be protected from unauthorized access by law. This is called Intellectual Property right(IPR). It enables to earn recognition, financial benefit, can sell the innovation, etc. It motivates further innovation.
Question 2.
Define the following terms.
- Cyberspace
- Cybercrime
Answer:
1. CyberSpace:
Earlier Traditional communication services such as postal service(Snail mail) are used for communication. It is a low speed and not reliable service. In order to increase the speed Telegram Services were used. Its speed was high but it has lot of limitations and expensive too.
Later telephones were used for voice communication. Nowadays telephone systems and computer systems are integrated and create a virtual(un real) environment. This is called cyberspace. The result of this integration is that tremendous speed and it is very cheap.
2. Cybercrime:
Just like normal crimes (theft, trespassing private area, destroy, etc,) Cybercrimes (Virus, Trojan Horse, Phishing, Denial of Service, Pornography, etc) also increased significantly. Due to cybercrime, the victims lose money, reputation, etc and some of them commit suicide.
Question 3.
Write a short note on
- Trademark
- Industrial design
Answer:
1. Trademark:
This is a unique, simple and memorable sign to promote a brand and hence increase the business and goodwill of a company. It must be registered. The period of registration is for 10 years and can be renewed. The registered trademark under Controller General of Patents Design and Trademarks cannot use or copy by anybody else.
2. Industrial designs:
A product or article is designed so beautifully to attract the customers. This type of designs is called industrial design. This is a prototype and used as a model for large scale production.
Question 4.
Compare patent and Trademark.
1. Patents:
A person or organization invented a product or a creation can be protected from unauthorized copying or creation without the permission of the creator by law. This right is called Patent. In India the validity of the right is up to 20 years. After this anybody can use freely.
2. Trademark:
This is a unique, simple and memorable sign to promote a brand and hence increase the business and goodwill of a company. It must be registered. The period of registration is for 10 years and can be renewed. The registered trademark under Controller General of Patents Design and Trademarks cannot use or copy by anybody else.
Question 5.
Write any one website for the following services.
- e-Governance
- e-Business
- e-Banking
- e-Learning
Answer:
- e-Governance(any One) www.dhsekerala.gov.in, www.incometaxindia.gov.in, www.spark.gov.in,www.ceo.kerala.gov. in
- e-Business www.indane.co.in, www.amazon.com,www.ebay.in
- e-Banking www.onlinesbi.co.in
- e-Learning www.ignouonline.ac.in,www.nptel.iitm.ac.in
Question 6.
Write a short note about EPS.
Answer:
Electronic Payment System(EPS): It is also called plastic money that is electronically exchanging money between two individuals or firms(buyers and sellers) in an online environment.
Question 7.
What is cyberspace?
Answer:
Earlier Traditional communication services such as postal service(Snail mail) are used for communication. It is a low speed and not reliable service. In order to increase the speed Telegram Services were used. Its speed was high but it has lot of limitations and expensive too.
Later telephones were used for voice communication. Nowadays telephone system and computer system are integrated and create a virtual(unreal) environment. This is called cyberspace. The result for this integration is that tremendous speed and it is very cheap.
Question 8.
Why is cyberspace called a virtual world?
Answer:
The telephone system and computer system are integrated and create a virtual(un real) environment. This is called cyber space. The result for this integration is that tremendous speed and it is very cheap. This is an imaginary world. We can see persons with different behaviour. Because of good and bad people we can’t believe blindly. If we search a solution for a problem thousands of answers will get instantly and may confused us.
Question 9.
What is copyright? How does it differ from patent?
Answer:
1. Copyright:
The trademark is ©, copyright is the property right that arises automatically when a person creates a new work by his own and by Law it prevents the others from the unauthorized or intentional copying of this without the permission of the creator for 60 years after the death of the author.
2. Patents:
A person or organization invented a product or a creation can be protected from unauthorized copying or creation without the permission of the creator by law. This right is called Patent. In India the validity of the right is up to 20 years. After this anybody can use freely.
Question 10.
Explain the exclusive right given to the owner by IPR?
Answer:
The exclusive right given to the owner by I PR is owner can disclose their creations for money.
Question 11.
it is the unauthorized copying, distribution, and use of a creation without the permission of the creator. It is against the copyright act and hence the person committed deserve the punishment.
Question 12.
Match the following

Answer:
a – 2
b – 3
c – 4
d – 1
Question 13.
What do you meant by infringement?
Answer:
Unauthorized copying or use of Intellectual property rights such as Patents, Copy rights and Trademarks are called intellectual property lnfringement(violation). It is a punishable offence.
Plus Two Computer Science ICT and Society Three Mark Questions and Answers
Question 1.
Write a short note on the importance of IT Act 2000.
Answer:
Information Technology Act 2000(amended in 2008):
IT Act 2000 controls the use of Computer(client), Server, Computer Networks, data and Information in Electronic format and provide legal infrastructure for E-commerce, in India. This is developed to promote IT industry, control e-commerce also ensures the smooth functioning of E-Governance and it prevents cyber crimes.
The person those who violate this will be prosecuted. In India, IT bill introduced in the May 2000 Parliament Session and it is known as Information Technology Act 2000. Some exclusions and inclusions are introduced in December 2008.
Question 2.
“Infomania affects peoples’ lives and their loved ones.”
Comment on this statement.
Answer:
Info mania is excessive desire(infatuation) for acquiring knowledge from various modern sources like Internet, Email, Social media. Instant Message Application(WhatsApp) and Smart Phones. Due to this the person may neglect daily routine such as family, friends, food, sleep, etc. hence they get tired.
They give first preference to Internet than others. They create their own Cyber World and no interaction to the surroundings and the family. They are more anxious and afraid that they will be out from the cyber world unless they updated.
Question 3.
Define the term e-Business. What are the advantages and challenges of e-Business? Write any two e-Business websites.
Answer:
E-business(electronic Business): Providing ser¬vices or running business through internet is called E-business.
Advantages of e-business:
- It overcomes geographical limitations
- It reduces the operational cost
- It minimizes the time and cost
- It remains open all the time
- We can locate the product faster from a wider range of choices
Challenges to E business - Peoples are unaware of IT applications and its uses
- Most peoples don’t have plastic money(credit / debit card) and net banking
- It requires high security measurements otherwise you may lose money
- We can’t touch or smell products through online
- Some companies may not have proper Goods delivery service
Useful e-Business websites
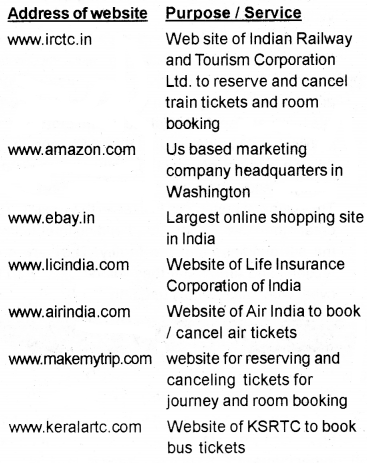
Question 4.
How do trademark and industrial design differ?
Answer:
Trademark:
This is a unique, sirhple and memorable sign to promote a brand and hence increase the business and goodwill of a company. It must be registered. The period of registration is for 10 years and can be renewed. The registered trademark under Controller General of Patents Design and Trademarks cannot use or copy by anybody else.
Industrial designs:
A product or article is designed so beautifully to attract the customers. This type of designs is called industrial design. This is a prototype and used as a model for large scale production.
Question 5.
Why is Cyberlaw important?
Answer:
Just like normal crimes (theft, trespassing private area, destroy, etc.) Cybercrimes (Virus, Trojan Horse, Phishing, Denial of Service, Pornography, etc.) also increased significantly. Due to cybercrime, the victims lose money, reputation, etc. and some of them commit suicide.
Cyberlaw ensures the use of computers and Internet by the people safely and legally. It consists of rules and regulations like Indian Penal Code (IPC) to stop crimes and for the smooth functions of Cyberworld. Two Acts are IT Act 2000 and IT Act Amended in 2008.
Question 6.
“Infomania has became a psychological problem”. Write your opinion.
Answer:
Info mania is the excessive desire(lnfatuation) for acquiring knowledge from various modern sources like Internet, Email, Social media, Instant Message Application(WhatsApp) and Smart Phones. Due to this the person may neglect daily routine such as family, friends, food, sleep, etc. hence they get tired.
They give first preference to Internet others. They create their own Cyber World and no interaction to the surroundings and the family. They are more anxious and afraid that they will be out from the cyber world unless they updated.
Plus Two Computer Science ICT and Society Five Mark Questions and Answers
Question 1.
“Due to anonymous nature of Internet it is possible for the people to engage in variety of criminal activities.” Justify the statement with special reference to cyber crimes taking place against individual.
Answer:
Cyber crimes against individuals
i. Identity theft:
The various information such as personal details(name, Date of Birth, Address, Phone number etc) , Credit / Debit Card details(Card number, PIN, Expiry Date, CW, etc), Bank details, etc. are the identity of a person. Stealing these information by acting as the authorized person without the permission of a person is called Identity theft. The misuse of this information is a punishable offence.
ii. Harassment:
Commenting badly about a particular person’s gender, colour, race, religion, nationality, in Social Media is considered as harassment. This is done with the help of Internet is called Cyber stalking (Nuisance). This is a kind of torturing and it may lead to spoil friend ship, career, self image and confidence. Sometimes may lead to a big tragedy of a whole family or a group of persons.
iii. Impersonation and cheating:
Fake accounts are created in Social Medias and act as the original ICT and Society one for the purpose of cheating or misleading others. Eg: Fake accounts in Social Medias (Facebook, Twitter, etc), fake SMS, fake emails etc.
iv. Violation of privacy:
Trespassing into another person’s life and try to spoil life. It is a punishable offence. Hidden camera is used to capture the video or picture and black mailing them.
v. Dissemination of obscene material: With the help of hidden camera capture unwanted video or picture. Distribute or publish this obscene clips on Internet without the consent of the victims may mislead the people specifically the younger ones.
Question 2.
Explain different categories of cyber crimes in detail.
Answer:
Just like normal crimes( theft, trespassing private area, destroy, etc,) Cyber crimes(Virus, Trojan Horse, Phishing, Denial of Service, Pornography etc) also increased significantly . Due to cyber crime, the victims lose money, reputation,etc and some of them commit suicide.
Answer:
A. Cyber crimes against individuals:
1. Identity theft:
The various information such as personal details(name, Date of Birth, Address, Phone number etc.), Credit / Debit Card details(Card number, PIN, Expiry Date, CW, etc), Bank details, etc. are the identity of a person. Stealing these information by acting as the authorized person without the permission of a person is called Identity theft. The misuse of this information is a punishable offence.
2. Harassment:
Commenting badly about a particular person’s gender, colour, race, religion, nationality, in Social Media is considered as harassment. This is done with the help of Internet is called Cyber stalking (Nuisance). This is a kind of torturing and it may lead to spoil friend ship, career, self image and confidence. Sometimes may lead to a big tragedy of a whole family or a group of persons.
3. Impersonation and cheating:
Fake accounts are created in Social Medias and act as the original one for the purpose of cheating or misleading others. Eg: F.ake accounts in Social Medias (Facebook, Twitter,etc), fake sms, fake emails, etc.
4. Violation of privacy:
Trespassing into another person’s life and try to spoil the life. It is a punishable offence. Hidden camera is used to capture the video or picture and black mailing them.
5. Dissemination of obscene material:
With the help of hidden camera capture unwanted video or picture. Distribute or publish this obscene clips on Internet without the consent of the victims may mislead the people specifically the younger ones.
B. Cyber crimes against property:
Stealing credit card details, hacking passwords of social media accounts or mail account or Net banking, uploading latest movies etc, are considered as cyber crimes against property.
1. Credit card fraud:
Stealing the details such as credit card number, company name, expiry date, cw number,password etc. and use these details to make payment for purchasing goods or transfer funds also.
2. Intellectual property theft:
The violation of Intellectual Property Right of Copy right, Trademark, Patent, etc. In film industry crores of investment is needed to create a movie. Intellectual Property thieves upload the movies on the Releasing day itself. Hence the revenue from the theatres are less significantly and undergoes huge loss.(Eg: Premam, Bahubali, etc) Copying a person’s creation and present as a new creation is called plagiarism. This can be identified some tools(programs) available in the Internet
3. Internet time theft:
This is deals with the misuse of WiFi Internet facility. If it is not protected by good password there is a chance of misuse our devices(Modem/Router) to access Internet without our consent by unauthorized persons. Hence our money and volume of data(Package) will lose and we may face the consequences if others make any crimes.
C. Cyber crimes against government:
The cyber crimes against Govt, websites is increased significantly. For example in 2015 the website of Registration Department of Kerala is hacked and destroys data from 2012 onwards.
1. Cyber terrorism:
It is deals with the attacks against very sensitive computer networks like computer controlled atomic energy power plants, air traffic controls, Gas line controls, telecom, Metro rail controls, Satellites, etc. This is a very serious matter and may lead to huge loss (money and life of citizens). So Govt, is very conscious and give tight security mechanism for their services.
2. Website defacement:
It means spoil or hacking websites and posting bad comments about the Govt.
3. Attacks against e-governance websites :
Its main target is a Web server. Due to this attack the Web server/ computer forced to restart and this results refusal of service to the genuine users. If we want to access a website first you have to type the web site address in the URL and press Enter key, the browser requests that page from the web server. Dos attacks send huge number of requests to the web server until it collapses due to the load and stops functioning.
Question 3.
“For the implementation of e-Learning different tools.
Answer:
e Learning tools
1. Electronic books reader(eBooks): With the help of a tablet or portable computer or any other device we can read digital files by using an s/w is called electronic books reader.
2. e-text: The electronic format of textual data is called e-Text.
3. Online chat: Realtime exchange of text or audio or video messages between two or more person over the Internet.
4. e-Content: The data or information such as text, audio, video, presentations, images, animations, etc, are stored in electronic format.
5. Educational TV channels: TV channels dedicated only for the e-Learning purpose.
Eg. VICTERS (Virtual Classroom Technology on Edusat for Rural Schools OR Versatile ICT Enabled Resources for Students)
