Kerala Plus Two Computer Application Notes Chapter 11 Trends and Issues in ICT
Mobile Computing
The drawbacks of Desk computers are, it is heavy and power consumption rate is high and it is not portable(not mobile).
The advancements in computing technology, lightweight and low power consumption have led to the developments of more computing power in handheld devices like laptops, tablets, smartphones, etc.
Nowadays instead of desktops, lightweight and low power consumption devices are used because they are cheap and common. Moreover people are able to connect to others through the internet even when they are in motion.
Mobile Communication
The term ‘mobile’ help people to change their lifestyles and become the backbone of society. Mobile communication networks do not require any physical connection.
Generations in mobile communication
The mobile phone was introduced in the year 1946. Early-stage it was expensive and limited services hence its growth was very slow. To solve this problem, cellular communication concept was developed in 1960’s at Bell Lab. 1990’s onwards cellular technology became a common standard in our country.
The various generations in mobile communication are
a) First Generation networks(1G):
It was developed around 1980, based on analog. system and only voice transmission were allowed.
b) Second Generation networks (2G):
This is the next-generation network that was allowed voice and data transmission. Picture message and MMS(Multimedia Messaging Service) was introduced. GSM and CDMA standards were introduced by 2G.
i) Global System for Mobile(GSM):
It is the most successful standard. It uses narrowband TDMA (Time Division Multiple Access), allows simultaneous calls on the same frequency range of 900 MHz to 1800 MHz. The network is identified using the SIM(Subscriber Identity Module).
GPRS (General Packet Radio Services): It is a packet-oriented mobile data service on the 2G on GSM. GPRS was originally standardized by European Telecommunications Standards
Institute (ETSI) GPRS usage is typically charged based on the volume of data transferred. Usage above the bundle cap is either charged per megabyte or disallowed.
EDGE (Enhanced Data rates for GSM Evolution): It is three times faster than GPRS. It is used for voice communication as well as an internet connection.
ii) Code Division Multiple Access (CDMA):
It is a channel access method used by various radio communication technologies. CDMA is an example of multiple access, which is where several transmitters can send information simultaneously over a single communication channel. This allows several users to share a band of frequencies To permit this to be achieved without undue interference between the users and provide better security.
c) Third Generation networks (3G):
It allows a high data transfer rate for mobile devices and offers high-speed wireless broadband services combining voice and data. To enjoy this service 3G enabled mobile towers and handsets required.
d) Fourth Generation networks (4G): It is also called Long Term Evolution(LTE) and also offers ultra-broadband Internet facility such as high quality streaming video. It also offers good quality image and videos than TV.
e) Fifth Generation networks (5G): This is the next-generation network and expected to come into practice in 2020. It is more faster and cost-effective than the other four generations. More connections can be provided and more energy efficient.
Mobile communication services
a) Short Message Service(SMS): It allows transferring short text messages containing up to 160 characters between mobile phones. The sent message reaches a Short Message Service Center(SMSC), that allows ‘store and forward’ systems. It uses the protocol SS7 (Signaling System No7). The first SMS message ‘Merry Christmas’ was sent on 03/12/1992 from a PC to a mobile phone on the Vodafone GSM network in the UK.
b) Multimedia Messaging Service (MMS): It allows sending Multi-Media(text, picture, audio, and video file) content using mobile phones. It is an extension of SMS.
c) Global Positioning System(GPS): It is a space-based satellite navigation system that provides location and time information in all weather conditions, anywhere on or near the Earth where there is an unobstructed line of sight to four or more GPS satellites. The system provides critical capabilities to military, civil, and commercial users around the world. It is maintained by the United States government and is freely accessible to anyone with a GPS receiver. GPS was created and realized by the U.S. Department of Defense (DoD) and was originally run with 24 satellites. It is used for vehicle navigation, aircraft navigation, ship navigation, oil exploration, Fishing, etc. GPS receivers are now integrated with mobile phones.

d) Smart Cards: A smart card is a plastic card with a computer chip or memory that stores and transacts data. A smart card (may be like your ATM card) reader used to store and transmit data. The advantages are it is secure, intelligent and convenient.
The smart card technology is used in SIM for GSM phones. A SIM card is used as identification proof.
Mobile operating system: It is an OS used in hand held devices such as smart phone, tablet, etc. It manages the hardware, multimedia functions, Internet connectivity,etc. Popular OSs are Android from Google, iOS from Apple, BlackBerry OS from BlackBerry and Windows Phone from Microsoft.
Android OS: It is a Linux-based OS for Touch screen devices such as smartphones and tablets.lt was developed by Android Inc. founded in Palo Alto, California in 2003 by Andy Rubin and his friends. In 2005, Google acquired this. A team led by Rubin devel¬oped a mobile device platform powered by the Linux Kernel. The interface of Android OS is based on touch inputs like swiping, tapping, pinching in, and out to manipulate on-screen objects. In 2007 onwards this OS is used in many mobile phones and tablets. An¬droid SDK(Software Development Kit) is available to create applications(apps) like Google Maps, FB, What’s App,etc. It is of open-source nature and many Apps are available for free download from the Android Play Store hence increase the popularity. Different Android Versions are shown below:
Version – Code name
4.4 – KitKat
4.1 – Jelly Bean
4.0.3 – Ice Cream Sandwich
3.1 – Honeycomb
2.3 – Gingerbread
2.2 – Froyo
2.0 – Eclair
1.6 – Donut
1.5 – Cupcake
ICT in business: Drastic developments in ICT have changed the shopping habits of people. Earlier people shops traditionally. But nowadays people buy products and services online. A study reveals that online shopping habits of people are increased. Aftersale service is also good, delivery of the products is prompt and safe. The status of the product can be tracked easily hence increase the confidence level of the online customers.
Social networks and big data analytics: Earlier before buying a product people may consult two or three shop keepers or local friends and take decisions. But nowadays before taking decisions, people search shopping sites, social network groups(Facebook, WhatsApp, Instagram, Twitter, etc), web portals, etc. for the best prices. Almost all online sites have product comparison menus. By this, we can compare the price, features, etc. Earlier a product is created and customers are forced to buy. But today customer is the King of the market, so products are created for the choices of the customers.
So companies gathering information about the customers from various sources such as social media like Internet forums, social blogs, Microblogs, etc. The volume of such data is very large and considered big data in business. With the help of an s/w analysis this big data and generate a report that contains all the information such as choices, taste, needs, status etc of a customer.
Business logistics: It is the management of the flow(transportation) of resources such as food, consumer goods, services, animals etc in a business between the point of origin(source) and the point of consumption (destination) in order to meet the needs of companies and customers. Business logistics consists of many more complexities. The effective use of hardware and software reduces the complexities faced in Business logistics.
For this the hardware used is RFID(Radio Frequency Identification) tag and the reader. It is like the bar code. The RFID tag contains all the details of a product and it consists of a combination of a transmitter and a receiver. The data stored in the RFID tag can be accessed by a special reader and to read the data no need for an RFID tag and reader in a line of site instead both are within a range.
This tag is used in Vehicles as a prepaid tag and makes the payments easier in Toll booths. Similarly, it is useful to take the Census of wild animals also.
Information Security: The most valuable to a company(An enterprise ora Bank, etc) is their data base hence it must be protected from accidental or unauthorised access by unauthorised persons
Intellectual Property Right: Some people spend lots of money, time body, and mental power to create some products such as a classical movie, album, artistic work, discoveries, invention, software, etc. These types of Intellectual properties must be protected from unauthorized access by law. This is called Intellectual Property right(IPR).
Paris convention held in 1883 protects Industrial Property
Berne Convention held in 1886 protects Literary and Artistic work.
World Intellectual Property Organisation(WIPO) in 1960, Guided by the United Nations(UN) ensures/protects the rights of creators or owners and rewarded for their creation.
A person or an organization can register their Intellectual property such as creations, trademarks, designs, etc.
Intellectual property is divided into two categories
- Industrial Property
- Copyright
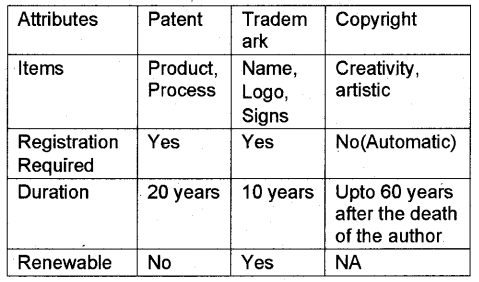
1) Industrial property: It ensures the protection of industrial inventions, designs, Agricultural products etc from unauthorized copying or creation or use. In India, this is done by the Controller of Patents Designs and Trademarks.
Patents: A person or organization that invented a product or creation can be protected from unauthorized copying or creation without the permission of the creator by law. This right is called Patent. In India, the validity of the right is up to 20 years. After this anybody can use it freely.
Trademark: This is a unique, simple and memorable sign to promote a brand and hence increase the business and goodwill of a company. It must be registered. The period of registration is for 10 years and can be renewed. The registered trademark under Controller General of Patents Design and Trademarks cannot use or^opy by anybody else.
Industrial designs: A product or article is designed so beautifully to attract customers. This type of design is called industrial design. This is a prototype and used as a model for large scale production.
Geographical indications: Some products are well known by the place of its origin. Kozhikkodan Halwa, Marayoor Sharkkara (Jaggery), Thirupathi Ladoo, etc are examples.
B) Copyright: The trademark is ©, copyright is the property right that arises automatically when a person creates a new work on his own, and by Law, it prevents the others from the unauthorized or intentional copying of this without the permission of the creator for 60 years after the death of the author.
Infringement (Violation): Unauthorized copying or use of Intellectual property rights such as Patents, Copyrights, and Trademarks are called intellectual property Infringement(violation). It is a punishable offense.
Patent Infringement: It prevents others from unauthorized or intentional copying or use of Patent without the permission of the creator.
Piracy: It is the unauthorized copying, distribution, and use of a creation without the permission of the creator. It is against the copy right act and hence the person committed deserves the punishment.
Trademark Infringement: It prevents others from unauthorized or intentional copying or use of Trademark without the permission of the creator.
Copy right Infringement: It prevents others from unauthorized or intentional copying or use of Copy right without the permission of the creator.
Cyberspace: Earlier Traditional communication services such as postal service(Snail mail) are used for communication. It is a low speed and not reliable service. In order to increase the speed Telegram Services were used. Its speed was high but it has lot of limitations and expensive too. Later telephones were used for voice communication. Nowadays telephone systems and computer systems are integrated and create a virtual(un real) environment. This is called cyberspace. The result of this integration is that tremendous speed and it is very cheap. The various departments of Govt, are providing speed, reliable and convenient online service hence increase productivity. Online shopping, Online banking, Online debate, Online Auction etc. are the various services offered by the Internet.
Through this one can transfer funds from our account to another account, hence one can pay bills such as telephone, electricity, purchase tickets(Flight, Train, Cinema, etc). As much as CyberSpace helps us that much as it gives us troubles.
Cyber Crimes: Just like normal crimes (theft, trespassing private area, destroy, etc,) Cybercrimes (Virus, Trojan Horse, Phishing, Denial of Service, Pornography etc) also increased significantly. Due to cybercrime, the victims lose money, reputation,etc and some of them commit suicide.
A) Cybercrimes against individuals
i) Identity theft: The various information such as personal details(name, Date of Birth, Address, Phone number etc), Credit / Debit Card details(Cand number, PIN, Expiry Date, CW, etc), Bank details, etc. are the identity of a person. Stealing this information by acting as the authorized person without the permission of a person is called Identity theft. The misuse of this information is a punishable offence.
ii) Harassment: Commenting badly about a particular person’s gender, colour, race, religion, nationality, in Social Media is considered as harassment. This is done with the help of the Internet is called Cyberstalking (Nuisance). This is a kind of torturing and it may lead to spoiling friendship, career, self-image and confidence. Sometimes may lead to a big tragedy of a whole family or a group of persons.
iii) Impersonation and cheating: Fake accounts are created in Social media and act as the original one for the purpose of cheating or misleading others. Eg: Fake accounts in Social Medias (Facebook, Twitter, etc), fake SMS, fake emails etc.
iv) Violation of privacy: Trespassing into another person’s life and try to spoil life. It is a punishable offense. A hidden camera is used to capture the video or picture and blackmailing them.
v) Dissemination of obscene material: With the help of hidden camera capture unwanted video or picture. Distribute or publish these obscene clips on the Internet without the consent of the victims may mislead people specifically the younger ones.
B) Cybercrimes against property: Stealing credit card details, hacking passwords of social media accounts or mail account or Net banking, uploading the latest movies etc, are considered as cyber crimes against property.
i) Credit card fraud: Stealing the details such as credit card number, company name, expiry date, CVV number, password etc. and use these details to make payment for purchasing goods or transfer funds also.
ii) Intellectual property theft: The violation of Intellectual Property Right of Copyright, Trademark, Patent, etc. In the film industry crores of investment are needed to create a movie. Intellectual Property thieves upload the movies on the Releasing day itself. Hence the revenue from the theatres is less significant and undergoes huge loss. (Eg: Premam, Bahubali, etc)
Copying a person’s creation and present as a new creation is called plagiarism. This can be identified as some tools(programs) available in the Internet
iii) Internet time theft: This is deals with the misuse of WiFi Internet facilities. If it is not protected by a good password there is a chance of misuse of our devices (Modem/Router) to access the Internet without our consent by unauthorized persons. Hence our money and volume of data(Package) will lose and we may face the consequences if others make any crimes.
C) Cybercrimes against the government: The cyber crimes against Govt, websites is increased significantly. For example in 2015 the website of the Registration Department of Kerala is hacked and destroys data from 2012 onwards.
i) Cyber terrorism: It deals with attacks against very sensitive computer networks like computer-controlled atomic energy power plants, air traffic controls, Gas line controls, telecom, Metro rail controls, Satellites, etc.. This is a very serious matter and may lead to a huge loss (money and life of citizens). So Govt is very conscious and give tight security mechanism for their services.
ii) Website defacement: It means to spoil or hacking websites and posting bad comments about the Govt.
iii) Attacks against e-governance websites: Its main target is a Web server. Due to this attack, the Web server/ computer forced to restart and this results in refusal of service to the genuine users. If we want to access a website first you have to type the web site address in the URL and press the Enter key, the browser requests that page from the webserver. Dos attacks send a huge number of requests to the webserver until it collapses due to the load and stop functioning.
Cyberethics
Guidelines for using computers over the internet
- Emails may contain Viruses so do not open any unwanted emails
- Download files from reputed sources(sites)
- Avoid clicking on pop-up Advt.
- Most of the Viruses spread due to the use of USB drives so use cautiously.
- Use a firewall on your computer
- Use anti-virus and update regularly
- Use spam blocking software
- Take backups in regular time intervals
- Use strong passwords, i.e a mixture of characters (a-z & A-Z), numbers, and special characters.
- Do not use bad or rude language in social media and emails.
- Untick ‘Remember Me’ before login.
CyberLaws: It ensures the use of computers and the Internet by people safely and legally. It consists of rules and regulations like the Indian Penal Code(IPC) to stop crimes and for the smooth functions of Cyberworld. Two Acts are IT Act 2000 and IT Act Amended in 2008
Information Technology Act 2000(amended in 2008)
IT Act 2000 controls the use of Computer(client), Server, Computer Networks, data, and Information in Electronic format and provides the legal infrastructure for E-commerce, in India.
This is developed to promote the IT industry, control e-commerce also ensures the smooth functioning of E-Governance and it prevents cyber crimes.
The person who violates this will be prosecuted. In India, the IT bill introduced in the May 2000 Parliament Session and it is known as the Information Technology Act 2000. Some exclusions and inclusions are introduced in December 2008
Cyber Forensics: Critical evidence of a particular crime is available in electronic format with the help of computer forensics. It helps to identify the criminal with help of blood, skin, or hair samples collected from the crime site?: DNA, polygraph, fingerprints are other effective tools to identify the accused person is the criminal or not.
Info mania: Right information at the right time is considered the key to success. The information must be gathered, stored, managed, and processed well. Infomania is excessive desire(infatuation) for acquiring knowledge from various modem sources like the Internet, Email, Social media, Instant Message applications (WhatsApp), and Smart Phones. Due to this, the person may neglect daily routines such as family, friends, food, sleep, etc. hence they get tired. They give first preference to the Internet than others. They create their own Cyber World and no interaction with the surroundings and the family.
