Kerala Plus Two Computer Application Model Question Papers Paper 1 with Answers
| Board | SCERT |
| Class | Plus Two |
| Subject | Computer Application |
| Category | Plus Two Previous Year Question Papers |
Time: 2 Hours
Cool off time : 15 Minutes
General Instructions to candidates
- There is a ‘cool off time’ of 15 minutes in addition to the writing time of 2 hrs.
- You are not allowed to write your answers nor to discuss anything with others during the ‘cool off time’.
- Use the ‘cool off time’ to get familiar with the questions and to plan your answers.
- Read questions carefully before you answering.
- All questions are compulsory and the only internal choice is allowed.
- When you select a question, all the sub-questions must be answered from the same question itself.
- Calculations, figures and graphs should be shown in the answer sheet itself.
- Malayalam version of the questions is also provided.
- Give equations wherever necessary.
- Electronic devices except non-programmable calculators are not allowed in the Examination Hall.
Part – A
Answer all the questions from 1 to 5 carry one score each: (Scores: 5 × 1 = 5)
Question 1.
Write a C++ statement to declare an array with size 25 to accept the name of a student.
Answer:
char name[25];
Question 2.
Name the following tags:
- To include a button in HTML
- To partition the browser window
Answer:
- <input type=”button”>
- <frameset>
Question 3.
Define Web Hosting
Answer:
Buying or renting storage space to store website in a web server and provide service(made available 24 × 7) to all the computers connected to the Internet. This is called web hosting.
Question 4.
Define BPR.
Answer:
Business Process Re-engineering: In general BPR is the series of activities such as rethinking and redesign the business process to enhance the enterprise’s performance such as reducing the cost(expenses), improve the quality, prompt, and speed(time-bound) service. BPR enhances the productivity and profit of an enterprise.
Question 5.
Name the intellectual property represented by the symbols ®, ©.
Answer:
® – Registered Trade Mark
© – Copy Right
Part – B
Answer any nine questions from 6 to 16 carry 2 scores each: (Scores : 9 × 2 = 18)
Question 6.
Define built-in functions. Give two examples.
Answer:
Some functions that are already available in C++ are called pre-defined or built-in functions.
- strlen() – to find the number of characters in a string(i.e. string length).
- strcpy() – It is used to copy the second string into the first string.
- strcat() – It is used to concatenate the second string into the first one.
- strcmp() – It is used to compare two strings and returns an integer.
Question 7.
Write the use of the following in HTML:
(a) <A Href=”http://www.dhsekerala.gov.in>DHSE</A>.
(b) <EMBEDsrc=song1.mp3></EMBED>
Answer:
(a) To link dhse portal. This is an example for external linking.
(b) This is used to include an audio file in our web page.
Question 8.
Name the tag and attribute needed to create the following lists in HTML:
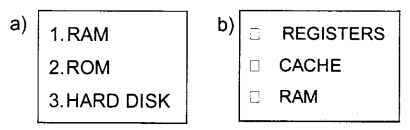
Answer:
a) <OL type=”1″>
b) <UL type=”square”>
Question 9.
Write a short note on free hosting.
Answer:
The name implies it is free of cost service and the expense is met by the advertisements. Some service providers allow limited facility such as limited storage space do not allow multimedia(audio and video) files.
A paid service website’s address is as follows
eg: www.bvmhsskalparamba.com
Usually, two types of free web hosting services as follows:
1) as a directory service.
Service provider’s website address/our website address
eg: www.facebook.com /bvm hss kalparambu
2) as a Subdomain
Our website address service providers website address
eg: bvmhsskalparamba.facebook.com
Question 10.
Write the type of web hosting that is most suitable:
- For hosting a school website with a database.
- For hosting a website for a firm
- For creating a blog to share pictures and posts
- For creating a low-cost personal website with a unique domain name.
Answer:
- Shared Hosting
- Dedicated Hosting
- Free Hosting
- VPS/Shared Hosting
Question 11.
Define the following:
(a) Field
(b) Record
Answer:
(a) Fields: the smallest unit of stored data.
eg: Regno, name, batch etc
(b) Record: Collection of related fields
eg: 101, Jose, Science
Question 12.
Write the name of any two-column constraints and their usage.
Answer:
Constraints are used to ensure database integrity.
- Not Null – It ensures that a column can never have NULL values.
- Unique – It ensures that no two rows have the same value in a column.
- Primary key – Similar to unique but it can be used only once in a table.
- Default – We can set a default value.
- Autojncrement – This constraint is used to perform auto_increment the values in a column. That automatically generates serial numbers. Only one auto_increment column per table is allowed.
Question 13.
Define the following ERP related technologies:
(a) CRM
(b) SCM
Answer:
(a) Customer Relationship Management (CRM): As we know the customer is the king of the market. The existence of a company mainly the customers. CRM consists of programs to enhance the customer’s relationship with the company.
(b) Supply Chain Management (SCM): This is deals with moving raw materials from suppliers to the company as well as finished goods from the company to customers. The activities include are inventory(raw materials, work in progress and finished goods) management, warehouse management, transportation management, etc.
Question 14.
Write a short note on SAP.
Answer:
SAP stands for Systems, Applications, and Products for data processing. It is a German MNCin Walldorf and founded in 1972. Earlier they developed ERP packages for large MNC. But nowadays they developed for small scale industries also.
Question 15.
Define the following terms:
(a) Trademark
(b) Copyright
Answer:
(a) Trademark: This is a unique, simple, and memorable sign to promote a brand and hence increase the business and goodwill of a company. It must be registered. The period of registration is for 10 years and can be renewed. The registered trademark under Controller General of Patents Design and Trademarks cannot use or copy by anybody else.
(b) Copyright: The trademark is ©, copyright is the property right that arises automatically when a person creates a new work on his own, and by Law, it prevents the others from the unauthorized or intentional copying of this without the permission of the creator for 60 years after the death of the author.
Question 16.
Name the following:
- Satellite-based Navigation system
- Service used to send messages with Multimedia content
- Packet oriented mobile data service on GSM.
- Smart card technology used only in GSM phone systems.
Answer:
- GPS
- MMS
- GPRS
- SIM
Part – C
Answer any nine questions from 17 to 27 carry 3 scores each: (Scores: 9 × 3 = 27)
Question 17.
Define Jump Statements. Explain any two.
Answer:
The execution of a program is sequential but we can change this sequential manner by using jump statements. The jump statements are
- goto statements: By using goto we can transfer the control anywhere in the program without any condition. The syntax is the goto label;
- break statement: It is used to skip over a part of the code i.e. we can premature exit from a loop such as while, do-while, for, or switch.
- continue statement: It bypasses one iteration of the loop.
- exit(0) function: It is used to terminate the program. For this, the header file cstdlib must be included.
Question 18.
Explain about nested loops.
Answer:
Nested Loop: A loop contains another loop completely then it is called a nested loop.
Eg.
#include<iostream>
using namespace std;
int main()
{
int i, j;
for(i=1; i<5; i++)
{
for(j=1; j<=i; j++)
cout<<"*";
cout<<endl;
}
}Question 19.
Compare call-by-value and call-by-reference methods for calling functions.
Answer:
| Call by Value | Call by Reference |
| Ordinary variables are used as formal parameter | Reference variables are used as formal parameters |
| A copy of the original value is passed | The original value is passed |
| Any change made by the function will not affect the original value | Any change made by the function will affect the original value |
| Separate memory location is needed for actual and formal variables | Memory of actual arguments is shared by formal arguments. |
Question 20.
Differentiate between local and global variables.
Answer:
| Local Variable | Global Variable |
| 1. Declared inside a block. | 1. Declared outside of all blocks. |
| 2. It cannot be used in any other block. | 2. It can be used anywhere in the program. |
| 3. Memory is allocated when the block is active. | 3. Memory is allocated when the program begins. |
| 4. Memory is de-allocated when the block is completed. | 4. Memory is de-allocated when the program terminates. |
Question 21.
Name any two attributes of the following tags:
(a) <HTML>
(b) <MARQUEE>
(c) <FONT>
Answer:
(a) Attributes of <HTML> are dir(direction ltr or rtl) and Language
(b) Attributes of <MARQUEE> (Any Two)
Height – Sets the height of the Marquee text
Width – Sets the width of the Marquee text
Direction – Specifies the scrolling direction of the text such as up, down, left or right
Behavior – Specifies the type such as Scroll, Slide(Scroll and stop) and alternate(to and fro).
<marquee behavior-“scroll”
scrollamount=”100″>hello</marquee>
<marquee behavior-“slide”
scrollamount=”100″>hello</marquee>
<marquee behavior-“alternate”
scrollamount=”100″>hello</marquee>
Scrolldelay – Specifies the time delay in seconds between each jump.
scrollamount – Specifies the speed of the text
loop – This specifies the number of times the marquee scroll. Default infinite.
bgcolor – Specifies the back ground colour.
Hspace – Specifies horizontal space around the marquee
Vspace – Specifies vertical space around the marquee
(c) <Font> used to specify the font characteristics. Its attributes are size, face, and color.
Question 22.
Name the three essential tags for creating a table in HTML. Write the purpose of each tag.
Answer:
- <Table> is used to create a table.
- <TR> is used to create a row.
- <TH> is used to create heading cells.
- <TD> is used to create data cells.
Question 23.
Rewrite the following C++ code in JavaScript:
void length ()
{
char str[ ]="WELCOME";
cout<<strl;
}Answer:
<html>
<head>
<Script Language="JavaScript">
function lengths()
{
var str1;
str1="WELCOME";
document.write(str1);
}
</script>
</head>
<body>
<center>
<form name="frm">
<input type="button" value="print" onClick="lengths()">
</form>
</center>
</body>
</html>Question 24.
Explain any three operators used in Relational algebra.
Answer:
Relational Algebra(Any Three)
- Select operation(s): It is used to select tuples in a relation that satisfies a condition.
- Project Operation (p): It is used to select certain columns while discards some other columns.
- Cartesian Product (X): All possible combinations of tuples from two relations.
- Union Operation (E): All tuples appearing in either or both of two relations.
- Intersection operation (Q): All tuples appearing in both relations.
- Set difference operation (-): All tuples appearing in the first relation and not in the second.
Question 25.
Explain any three advantages of DBMS.
Answer:
Advantages of DBMS (Any Three)
1. Data Redundancy: It means duplication of data. DBMS eliminates redundancy. DBMS does not store more than one copy of the same data.
2. Inconsistency can be avoided: If redundancy occurs there is a chance to inconsistency. If redundancy is removed then inconsistency cannot occur.
3. Data can be shared: The data stored in the database can be shared by the users or programs.
4. Standards can be enforced – The data in the database follows some standards.
Eg: a field ‘Name’ should have 40 characters long. Some standards are ANSI, ISO, etc.
5. Security restrictions can be applied – The data is of great value so it must be kept secure and private. Data security means the protection of data against accidental or intentional disclosure or unauthorized destruction or modification by an unauthorized person.
6. Integrity can be maintained: It ensures that the data is to be entered in the database is correct.
7. Efficient data access: It stored a huge amount of data efficiently and can be retrieved whenever a need arise.
8. Crash recovery: Sometimes all or a portion of the data is lost when a system crashes. A good DBMS helps to recover data after the system crashed.
Question 26.
Define the following:
(a) DML
(b) DDL
(c) DCL
Answer:
(a) DML – DML means Data Manipulation Language.
It is used to insert records into a table, modify the records of a table, delete the records of a table, and retrieve the records from a table.DML commands are select, insert, delete, and update.
(b) DDL – DDL means Data Definition Language.
It is used to create the structure of a table, modify the structure of a table, and delete the structure of a table. DDL commands are created, alter and drop
(c) DCL – DCL means Data Control Language.
It is used to control access to the database. Commands are Grant, Revoke, etc
Question 27.
Write the result of the following:
(a) ALTER TABLE <table name>
Drop <column name>
(b) DELETE FROM <table name>
(c) DROP TABLE <table name>
Answer:
(a) This command is used to delete a column from a table.
(b) This command is used to delete all the records from a table.
(c) This command is used to delete a table from the memory.
Part – D
Answer any two questions from 28 to 30 with 5 scores each: (Scores: 2 × 5 = 10)
Question 28.
Consider the following C++ code
int main()
{
char str[20];
cout<<"Enter a String";
cin>>str;
puts(str);
return 0;
}- Write the value of str if the string ‘HELLO WORLD’ is input to the code. Justify.
- Write the amount of memory allocated for storing the array str. Give reason.
- Write an alternative we can use to input string in place of cin
Answer:
- The output is “HELLO”.Here the white space after HELLO is treated as the delimiter hence the remaining(“WORLD”) will be truncated.
- 20 bytes of memory is allocated for storing the array str.
- gets() or getline() can be used to input string for accepting white spaces.
Question 29.
In HTML
(a) Differentiate client-side script and server-side script
(b) Name the tag and its attribute used to include a script in a web page
(c) Name any two server-side scripting language.
Answer:
(a)
| Client-Side Scripting | Server Side Scripting |
| The script is copied to the client browser | The script is copied to the webserver |
| Executed by the client | Executed by the server and result is get back to the browser window |
| Used for Client level validation | Connect to the database in the server |
| It is possible to block by the user | Cannot possible |
| Client-side scripts depend on the type and version of the browser | It does not depend on the type and version of the browser |
(b) <SCRIPT Language=”JavaScript”>
(c) ASP, JSP, PHP, etc.
Question 30.
In JavaScript:
(a) Explain any three types of operators used.
(b) Describe any two datatypes used.
Answer:
(a) Operators in JavaScript: Operators are the symbols used to perform an operation
- Arithmetic operators: It is a binary operator. It is used to perform addition(+), subtraction(-), division(/), multiplication(*), modulus(%-gives the remainder)
- Assignment operator: If a = 10 and b = 3 then a = b. This statement sets the value of a and b are the same, i.e. it sets a to 3.
- Logical operators: Here AND(&&), OR(||) are binary operators and NOT(!) is a unary operator. It is used to combine relational operations and it gives either true or false
b) Data types in JavaScript: Unlike C++ it uses only three basic data types
- Number: Any number(whole or fractional) with or without a sign.
Eg: +1977, -38.0003, -100, 3.14157,etc - String: It is a combination of characters enclosed within double-quotes.
Eg: “BVM”, “[email protected]”, etc - Boolean: We can store either true or false. It is case sensitive. That means can’t use TRUE OR FALSE
