Kerala Plus One Computer Science Previous Year Question Paper March 2019 with Answers
| Board | SCERT |
| Class | Plus One |
| Subject | Computer Science |
| Category | Plus One Previous Year Question Papers |
Time Allowed: 2 hours
Cool off time: 15 Minutes
Maximum Marks: 60
General Instructions to Candidates:
- There is a ‘cool off time’ of 15 minutes in addition to the writing time of 2 hours.
- Use the ‘cool off time’ to get familiar with the questions and to plan your answers.
- Read questions carefully before you answering.
- Read the instructions carefully.
- Calculations, figures, and graphs should be shown in the answer sheet itself.
- Malayalam version of the questions is also provided.
- Give equations wherever necessary.
- Electronic devices except non-programmable calculators are not allowed in the Examination Hall.
Answer all questions from 1 to 5. Each carry 1 score. (5 × 1 = 5)
Question 1.
The number of symbols used in a number system is ………….
Answer:
Base or Radix
Question 2.
Small and fast memory between processor and RAM is called ………….
Answer:
Cache memory
Question 3.
What is the use of Rhombus symbol in flowchart?
Answer:
Decision making or condition checking
Question 4.
To find the number of characters in a string, …………. function is used.
Answer:
strlen()
Question 5.
To check an alphabet is lowercase, ………. function can be used.
Answer:
islower()
Answer any 9 questions from 6 to 16. Each carries 2 scores. (9 × 2 = 18)
Question 6.
Expand the following:
a) ENIAC
b) VLSI
Answer:
a) Electronic Numeric Integrator and Calculator
b) Very Large Scale Integrated
Question 7.
State De’Morgan’s theorems.
Answer:
(A + B)’ = A’.B’
(A.B)’ = A + B’
Question 8.
Name any four e-Waste disposal methods.
Answer:
e-Waste disposal methods:
- Reuse: Reusability has an important role of e-Waste management and can reduce the volume of e-Waste.
- Incineration: It is the process of burning e-Waste at high temperature in a chimney
- Recycling of e-Waste: It is the process of making new products from this e-Waste.
- Land filling: It is used to level pits and cover by thick layer of soil.
Question 9.
Compare Entry Controlled loop with Exit Controlled loop.
Answer:
An entry controlled loop first checks the condition and execute(or enters into) the body of loop only if it is true. But exit control loop first execute the body of the loop once even if the condition is false then check the condition. The for loop and while loop are entry controlled loops but do-while loop is an exit controlled loop.
Question 10.
Find the invalid identifier names from the following: A1, d-w, 999, qwA, Z$, AaA1,8c
Answer:
Invalid identifiers
d-w(Special characters not allowed)
999(Cannot be start with a number)
z$($ not allowed)
8c(Cannot be start with a number)
Question 11.
List the data type modifiers used in C++.
Answer:
With the help of type modifiers, we can change the sign and range of data with same size. The important modifiers are signed, unsigned, long and short.
Question 12.
Write the symbols of the following C++ operators.
a) Conditional operator
b) Extraction operator
c) Increment operator
d) NOT operator
Answer:
a) ?:
b) <<
c) ++
d) !
Question 13.
Write the syntax of if ………… else statement.
Answer:
if(Test expression)
{
statement block 1;
}
else
{
statement block 2;
}
Question 14.
Compare Linear search with Binary search.
Answer:
| Linear | Binary |
| 1. No need of sorted array | 1. Need of sorted array |
| 2. Searching is slower for larger array. | 2. It is faster |
| 3. It starts checking from the first element and checks all elements. | 3. Divide and conquer method used |
Question 15.
What do you mean by argument of a function?
Explain formal arguments.
Answer:
To invoke a function that requires some data for performing the task, such data is called parameter or argument.
The parameters appear in a function definition are formal arguments.
Question 16.
Write the advantages of social media.
Answer:
Advantages of social media.
- Bring people together: It allows people to maintain the friendship
- Plan and organize events: It allows users to plan and organize events.
- Business promotion: It helps the firms to promote their sales.
- Social skills: There is a key role of the formation of society.
Answer any 9 questions from 17 to 27. Each carries 3 scores. (9 × 3 = 27)
Question 17.
Explain any three generations of computers.
Answer:
There are five generations of computers from 16th century to till date.
- First generation computers (1940-1956): Vacuum tubes were used in first generation computers. The input was based on punched cards and paper tapes and output was displayed on printouts.
- Second generation computers (1956-1963): Transistors, instead of Vacuum tubes, were used in 2nd generation computers hence size became smaller, less expensive, less electricity consumption and heat emission and more powerful and faster.
- Third generation computers (1964-1971): Integrated Circuits(IC’s) were used. IC’s or silicon chips were developed by Jack Kilby, an engineer in Texas Instruments. It reduced the size again and increased speed and efficiency.
- Fourth generation computers (1971 onwards): Microprocessors are used hence computers are called microcomputers.
- Fifth generation computers (future): Fifth generation computers are based on Artificial Intelligence(AI). Alis the ability to act as human intelligence like speech recognition, face recognition, robotic vision and movement etc.
Question 18.
Draw the logic circuit of Boolean expression X.Y + \(\bar{Y}\)
Answer:
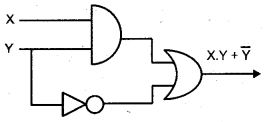
Question 19.
Convert (11011)2 to Octal decimal and Hexadecimal number systems.
Answer:
a) To octal-for this divide the number into groups of 3 bits starting from the right and. write down the corresponding octal equivalent
011 011 → 33
(11011)2 = (33)8
b) To decimal – for this multiply each digit by its corresponding weight and sum it up.
(11011)2 = (27)10
c) To Hexadecimal – for this divide the number into groups of 4 bits starting from the right and write down the corresponding hexadecimal equivalent
0001 1011 → 1B
(11011)2 = (1B)16
Question 20.
Name the steps involved in problem solving.
Answer:
- Problem identification
- Deriving the steps to obtain the solution.
- Coding
- Translation
- Debugging
- Execution and Testing
- Documentation
Question 21.
Write a short note on C++ character set.
Answer:
The character set of C++ is given below
a) Letters – A to Z and a to z.
b) Digits – 0 to 9
c) Special characters – +,-,*,/ etc
d) White spaces(non printable characters) and other characters.
Question 22.
Describe three types of C++ expressions with an example.
Answer:
An expression is composed of operators and operands
- Arithmetic – It consists of arithmetic operators and operands eg. a+5, b%10, etc
- Relational – It consists of relational operators and operands eg. a>5, b==5, etc
- Logical – It combines two or more relational expressions with logical operators. Eg. x>y && x==z
Question 23.
Write an algorithm for selection sort.
Answer:
Selection sort: In selection sort the array is divided into two parts, the sorted part and unsorted part. First smallest element in the unsorted part is searched and exchanged with the first element. Now there is 2 parts sorted part and unsorted part. This process continues.
Algorithm:
Step 1. Start
Step 2. Read N(The number of elements)
Step 3. Read N elements into the Array AR
Step 4. Repeat steps 5 to 8, (N-1) times
Step 5. Assume that the first element is the smallest and set into MIN, and its position is POS
Step 6. Repeat Step 7 until the last element of the list
Step 7. Compare MIN with the remaining elements and the smaller one is stored in the MIN(Swap) and its position in POS
Step 8. Revise the list by excluding the first element in the list
Step 9. Print the Sorted Array AR
Step 10. Stop.
Question 24.
Differentiate between put () and write () with an example.
Answer:
put() – This is used to print a character on the screen.
Eg. pout.put(“A”);
write() – This is used to print a string with specified length on the screen. Eg. cout.write(str,len);
Question 25.
Describe the merits of modular programming.
Answer:
Merits of modular programming is
- It reduces the size of the program
- Less chance of error
- It reduces programming complexity
- It improves reusability
Question 26.
Write short notes on
a) Bluetooth
b) Wi-Fi
c) Satellite
Answer:
a) Bluetooth: This technology uses radio waves in the frequency range of 2.402 GHz to 2.480 GHz. And transmit data in short distance. Mobile phones, Laptops, tablets etc use Bluetooth technology to transmit data.
b) Wi-Fi(Wireless Fidelity): It uses radio Waves to transmit information across a network in a range 2.4 GHz to 5 GHz in short distance. Nowadays this technology is used to access internet in Laptops, Desktops, tablets, Mobile phones etc.
c) Satellites: By using satellite we can communicate from any part of the world to any other. The ground stations are connected via satellite. The data signals transmitted from earth to satellite (uplink) and from the satellite to the earth (downlink).
Question 27.
What is the role of Firewall and Anti-virus scanner in computer networks?
Answer:
Firewall: It is a system that controls the incoming and outgoing network traffic by analyzing the data and then provides security to the computer network in an organization from other networks (internet).
Antivirus scanners: It is a tool used to scan computer files for viruses, worms and Trojan horses and cure the infected system. If any fault found it stops the file from running and stores the file in a special area called Quarantine(isolated area) and can be deleted later.
Answer any 2 questions from 28 to 30. Each carries 5 scores. (2 × 5 = 10)
Question 28.
a) Write any two examples of optical storage devices.
b) Rearrange the following memories in descending order depending on their speed.
(Hard disk, RAM, Cache Memory, Registers)
c) List four major functions of operating system.
Answer:
a) CD, DVD, Blue Ray Disc
b) Registers, Cache Memory, RAM, Hard Disk
c) Process management, Memory handling, Device management and file management
Question 29.
a) Explain any three jump statements with examples.
b) Read the following C++ statement and rewrite using if……. else.
(a>b)? cout<<a:
cout<<b;
Answer:
a) 1) goto statement:- By using goto we can transfer the control anywhere in the program without any condition. The syntax is goto label;
Eg.
#include<iostream>
using namespace std;
int main()
{
float a,b;
cout<<“Enter 2 numbers”;
cin>>a>>b;
if(b==0)
goto end;
cout<<“The quotient is “<<a/b;
return 0;
end:cout<<“Division by zero error”;
}
2) break statement:- It is used to skip over a part of the code i.e. we can premature exit from a loop such as while, do-while, for or switch.
Eg.
#include<iostream>
using namespace std;
main()
{
int i=1;
while(i<10)
{
cout<<i<<endl;
if(i==5)
break;
i++;
}
}
3) continue statement:- It bypasses one iteration of the loop.
Eg.
#include<iostream>
using namespace std;
main()
{
int i=0;
while(i<10)
{
i++;
if(i==5) continue;
cout<<i<<endl;
}
}
b) if(a>b)
cout<<a;
else
cout<<b;
Question 30.
Explain the network topologies with diagrams.
Answer:
The major topologies developed are star, bus, ring, tree and mesh.
1) Star Topology: A star topology has a server all other computers are connected to it. If computer A wants to transmit a message to computer B. Then computer A first transmit the message to the server then the server retransmits the message to the computer B. That means all the messages are transmitted through the server. Advantages are add or remove workstations to a star network is easy and the failure of a workstation will not effect the other: The disadvantage is that if the server fails the entire network will fail.
2) Bus Topology: Here all the computers are attached to a single cable called bus. Here one computer transmits all other computers listen. Therefore it is called broadcast bus. The transmission from any station will travel in both the direction. The connected computers can hear the message and check whether it is for them or not.
Advantages are add or remove computer is very easy. It requires less cable length and the installation cost is less. Disadvantage is fault detection is very difficult because of no central computer.
3) Ring Topology: Here all the computers are connected in the shape of a ring and it is a closed loop. Here also there is no central computer. Here a computer transmits a message, which is tagged along with its destination computer’s address. The message travels in one direction and each node check whether the message is for them. If not, it passes to the next node.
It requires only short cable length. If a single node fails, at least a portion of the network will fail. To add a node is very difficult.
4) Hybrid Topology: It is a combination of any two or more network topologies, Tree topology and mesh topology can be considered as hybrid topology.
a) Tree Topology: The structure of a tree topology is the shape of an inverted tree with a central node and branches as nodes. It is a variation of bus topology. The data transmission takes place in the way as in bus topology. The disadvantage is that if one node fails, the entire, portion will fail.
b) Mesh Topology: In this topology each node is connected to more than one node. It is just like a mesh (net). There are multiple paths between computers. If one path fails, we can transmit data through another path.
