Kerala Plus One Computer Science Chapter Wise Questions and Answers Chapter 12 Internet and Mobile Computing
Plus One Internet and Mobile Computing One Mark Questions and Answers
Question 1.
A network of smaller networks that exists all over the world is called ____________
Answer:
Internet
Question 2.
ARPANET means ______
Answer:
Advanced Research Projects Agency Network
Question 3.
Odd one out.
(a) Internet explorer
(b) Mozilla
(c) Netscape navigator
(d) Windows Explorer
Answer:
(d) Windows explorer, the others are browsers.
Question 4.
Odd man out.
(a) Word
(b) Excel
(c) PowerPoint
(d) Mosaic
Answer:
(d) Mosaic. It is a browser, others are MS Office packages.
Question 5.
The interface between user and computer hardware is called operating system then what about the interface between user and internet (www)?
Answer:
Browser
Question 6.
With the help of this the user can search informations provided on the internet. What is it?
Answer:
Browser.
Question 7.
Benhur wants to navigate through the web pages from the following which will help him?
(a) A browser
(b) MS Word
(c) Tally
(d) Paint
Answer:
(a) A browser
Question 8.
I am a piece of software. With the help of me a user can search information from the internet and navigate through the web pages. Who am I?
Answer:
Browser
Question 9.
Anil told you that he was browsing at that time. From the following choose the right one.
(a) He was visiting a website
(b) He was reading a book
(c) He was watching TV
(d) He was sleeping
Answer:
(a) He was visiting a website. The process of visiting a website is called browsing.
Question 10.
___________ is a popular browser commonly used in windows operating system.
(a) Mozilla
(b) Netscape navigator
(c) Mosaic
(d) Internet explorer
Answer:
(d) Internet Explorer
Question 11.
___________ browser is commonly used in Linux.
(a) Internet explorer
(b) Mozilla
(c) Netscape navigator
(d) Mosaic
Answer:
(b) Mozilla
Question 12.
Mr. Asokan wants to go the previous page. From the following which option will help him?
(a) Back button
(b) Refresh
(c) Favorites
(d) Stop
Answer:
(a) Back and forward button
Question 13.
While navigating through a website, sita wants to go back to the home page. From the following which will help her?
(a) Refresh
(b) Search
(c) Home
(d) Mail
Answer:
(c) Home
Question 14.
While surfing a website, Joyson wants to play music or video. Which button will help him?
(a) Home
(b) Search
(c) Media
(d) Mail
Answer:
(c) Media
Question 15.
Purnima wants to know the websites that her brother had visited last week? From the following which will help her?
(a) Media
(b) History
(c) Mail
(d) Search
Answer:
(b) History
Question 16.
While browsing, the internet connection is lost so you want to reload the web page. Which will help for this?
(a) Refresh
(b) Stop
(c) Media
(d) Edit
Answer:
(a) Refresh
Question 17.
The address bar is also known as _________
(a) URL
(b) UDL
(c) KRL
(d) None of these
Answer:
(a) URL
Question 18.
You want to add and organize a website to a list. Which will help for this?
(a) Favorites
(b) Search
(c) Back
(d) Mail
Answer:
(a) Favorites
Question 19.
How can it possible to understand that the browser is retrieving data?
(a) Access indicator icon animates
(b) From the refresh button
(c) From the back button
(d) None of these
Answer:
(a) Access indicator icon animates
Question 20.
The progress of the data being downloaded indicates by the ____________
(a) Address bar
(b) Progression bar
(c) Status bar
(d) None of these
Answer:
(c) Status Bar
Question 21.
Baby wants to download a file The time needed for that depends on the _________ of the file.
(a) Size
(b) Place
(c) Type
(d) None of these
Answer:
(a) Size
Question 22.
Kasim wants to print data on a A4 size paper. From the following which option will help him for that?
(a) Copy
(b) Page setup
(c) Search
(d) Media
Answer:
(b) Page setup
Question 23.
Mr. Franco’s e-mail id is [email protected]. He wants to connect this page fastly. From the following which will help him.
(a) Favorite
(b) Search
(c) Refresh
(d) Media
Answer:
(a) Favorite
Question 24.
Mrs. Janaki purchased a product through online and payment was given by credit card. She wants to protect the information about the credit card. How can it be possible from the following?
(а) Security
(b) Favorite
(c) Media
(d) Content
Answer:
(a) Security
Question 25.
Odd man out.
(a) www.google.com
(b) www.yahoo.com
(c) www.altavista.com
(d) www.stmaryshss.com
Answer:
(d) www.stmaryshss.com, the others are search engines.
Question 26.
Alvis got email about some products without his consent. Which type of email is this?
Answer:
Spam
Question 27.
What is the primary thing you have needed to sent an email to your friend?
Answer:
You have need an email id (address)
Question 28.
There is a PTA meeting in your school in the next month. The school authorities want to send the invitation to the parents. Which field of the message structure will help for this?
Answer:
CC or bcc
Question 29.
You want to send an invitation to your friends But the friends should not know that the same invitation is sent by you to others also. Which field of the message structure will help you?
Answer:
bcc
Question 30.
Mr. Lijo wants to send his photograph to his friend by email. Which feature will help him for this?
Answer:
Attachment feature
Question 31.
You got some pictures of Jesus Christ through email from one of your friends. You want to send this pictures to your brother. What button will help you for this?
Answer:
Forward button
Question 32.
You got an email from your father working abroad. You want to send an email without typing his email id. Which button will help you for this?
Answer:
Reply button
Question 33.
You got an email from an Insurance Company you want to store their email id which feature will help you for this?
Answer:
We can add address to Address Book.
Question 34.
Who proposed the idea of www.
Answer:
Tim Berners Lee
Question 35.
The protocol for internet communication is ___________
Answer:
TCP/IP protocol
Question 36.
A short distance wireless Internet access method is ___________.
Answer:
Wi-Fi
Question 37.
Give an example for an e-mail address.
Answer:
[email protected]
Question 38.
Which of the following is not a search engine?
(а) Google
(b) Bing
(c) Face book
(d) Ask
Answer:
(c) Facebook
Question 39.
Name the protocol used for e-mail transmission across Internet.
Answer:
Simple Mail Transfer Protocol(SMTP)
Question 40.
Name three services over Internet.
Answer:
WWW, Search engine, Engine
Question 41.
Each document on the web is referred using ___________
Answer:
Uniform Resource Locator(URL)
Question 42.
The small text files used by browsers to remember our email id’s, user names, etc are known as ____________.
Answer:
Cookies
Question 43.
The act of breaking into secure networks to destroy data is called ___________ hacking.
Answer:
Black hats
Question 44.
SIM is _______
(a) Subscriber Identity Module
(b) Subscriber Identity Mobile
(c) Subscription Identity Module
(d) Subscription Identity Mobile
Answer:
(a) Subscriber Identity Module
Question 45.
The protocol used to send SMS message is _________
Answer:
SS7(Signalling System No.7)
Question 46.
- Define Intranet
- Write the structure of an e-mail address. (1)
Answer:
- Intranet: A private network inside a company or organisation is called intranet,
- The structure of the email address is given below username@domainname
eg: [email protected]
Question 47.
- Acquiring information such as username, password, credit card details etc. using misleading websites is known as _______
- Pick the odd one out:
Google, Safari, Mozilla Firefox, Internet explorer.
Answer:
- Phishing
- Google it is a search engine All others are web browsers
Question 48.
Bluetooth can be used for _________ communication
(i) long distance
(ii) short distance
(iii) mobile phone
(iv) all of these
Answer:
(ii) short distance/(iii) mobile phone
Question 49.
Pick the odd one from the following list
(a) Spam
(b) Trojan horse
(c) Phishing
(d) Firewall
Answer:
(d) Firewall
Question 50.
_________ are small text files that are created in our computer when we use a browser to visit a website.
Answer:
cookies
Question 51.
Which one of the following technologies is used for locating geographic positions according to satellite based navigation system?
(a) MMS
(b) GPS
(c) GSM
(d) SMS
Answer:
(b) GPS
Plus One Internet and Mobile Computing Two Mark Questions and Answers
Question 1.
While walking on the road, Simran saw a notice board contains a text “Browsing” in front of a shop. What is Browsing?
OR
Roopa’s mother told you that Roopa is browsing in her room. What is browsing?
Answer:
The process of visiting the websites of various companies, organization, government, individuals etc is called internet browsing or surfing with the help of a browser software we can browse websites.
Question 2.
How can we know that the browser is working or not?
Answer:
The access indicator icon on the right corner of menu bar animates (rotates), when the browser is retrieving data or working. It is static when the browser is not working.
Question 3.
Discuss the steps to download a file from the website.
Answer:
To download a file from the website click on the link or button provided in the web page, then a dialog box will display. Enter the file name and specify the folder to which the file is to be saved. Then click save button then a window showing the progress of the downloading.
Question 4.
What is a Spamming?
Answer:
Sending an email without recipient’s consent to promote a product or service is called spamming. Such an email is called a spam.
Question 5.
You want to send a picture drawn using MS paint immediately to your friend. What method will you adopt for this, so that your friend receives it within seconds? Explain the steps to perform this operation.
Answer:
E-mail (Electronic mail) can be used. There is a facility called attachment will help you to send files with E-mail to your friend. First open your mail box, then take the option to write mail. Fill the email id and subject in the text boxes namely To and Sub respectively.
You can type text in the area given below. Then press the option attachments then select the picture file then press done and press send button.
Question 6.
What do you mean by an ‘always on’ connection?
Answer:
Wired broadband connection is called ‘always on’ connection because it does not need to dial and connect.
Question 7.
What are wikis?
Answer:
In this we can give our contributions regarding various topics and others can watch and edit the content. So incorrect information, advt, etc. are removed quickly.
eg: www.wikipedia.org.
Question 8.
How does a Trojan horse affect a computer?
Answer:
It appears as a useful software but it is a harmful software and it will delete useful software or files in a computer.
Question 9.
How can multimedia content be sent using mobile phones.
Answer:
MMS (Multi-Media Service) allows sending Multi-Media(text, picture, audio and video file) content using mobile phones. It is an extension of SMS.
Question 10.
What are the functions of a mobile OS?
Answer:
Mobile OS manages the hardware, multimedia functions, Internet connectivity, etc. Popular OSs are Android from Google, iOS from Apple, BlackBerry OS from BlackBerry and Windows Phone from Microsoft.
Question 11.
1. Observe the two figures given
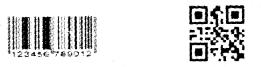
- Write their names
- What are their uses?
- Name the device associated with them.
2. RAM cannot be replaced by hard disk in a computer. Why?
Answer:
1. Their names are
- Bar code, QR code
- This is used to store all the information about a product such as name, price, batch, Exp. date etc.
- Barcode Reader, Mobile camera (Mobile camera can be used to read QR code information).
2. RAM means Random Access Memory. It is also called read and write memory. It is used to store operating system, and other programs, The one and only memory that the processor can be accessed is the primary memory. Hence RAM cannot be replaced by hard disk in a computer.
Question 12.
Explain “DOS attack’’ on servers.
Answer:
Denial of Service(DoS) attack:
Its main target is a Web server. Due to this attack the Web server/computer forced to restart and this results refusal of service to the genuine users.
If we want to access a website first you have to type the web site address in the URL and press Enter key, the browser requests that page from the web server. Dos attacks send huge number of requests to the web server until it collapses due to the load and stops functioning.
Question 13.
Find the best matches from the given definitions for the terms in the given list.
(Worm, Hacking, Phishing, Spam)
- Unsolicited emails sent indiscriminately.
- A technical effort to manipulate the normal behavior of networked computer system.
- A stand alone malware program usually makes the data traffic slow.
- Attempt to acquire information like usernames and passwords by posing as the original website.
- Appear to be a useful software but will do damage like deleting necessary files.
Answer:
Worm – 3
Hacking – 2
Phishing – 4
Spam – 1
Plus One Internet and Mobile Computing Three Mark Questions and Answers
Question 1.
What is a browser?
Answer:
A browser is a piece of software that acts as an interface between the user and the internal working of the internet. With the help of a browser the user can search information on the internet and it allows user to navigate through the web pages. The different browsers are
- Microsoft internet explorer
- Mozilla
- Netscape Navigator
- Mosaic
- Opera
Question 2.
Mr. Anirudhan wants to visit the website of Manorama. Their website address is www. manoramaonline.com. How can it be possible?
Answer:
To visit the website of manorama. Anirudhan has to type “www.manoramaonline.com” in the address bar and press the enter key or use the go button. Then the home page of manorama will display. Sometimes while typing the website address on the browser automatically searches and display the homepage.
Question 3.
The education Dept, of Govt, of Kerala declared SSLC results and it is available on the internet your friend wants to save the result in his computer. Help him to do so. .
Answer:
To save the result in his computer to a file by using the ‘save’ or ‘save as’ option of the file menu. When click this option a dialog box will appear then specify the folder whereas the file has to be saved using the dialog box and click OK. To save an image right click on the image, a pop-up menu will appear then choose the save option give a name and press OK.
Question 4.
The application form of Kerala entrance exam can be downloaded from the official website of Kerala govt. What do you mean by downloading?
Answer:
Downloading is the transfer of files or data from one computer to another usually from a server com¬puter to a client computer. The time required to download the file depends on the size of the file. The files may be text, graphics, program, movies, music, etc.
To download a file click on the link or button provided in the web page and specify the folder and filename and there is a window that shows the progress of the file being downloaded.
Question 5.
To apply minority scholarship, a student has to enter his details online, take a printout of this web page then send the application form with this printout to the authorities. Explain how to take a printout of a web page ?
Answer:
To print a web page either select the print command from file menu or use the print button on the standard tool bar. The page setup option is provided in the file menu. It helps to specify the paper size, margins header and footer and also the page orientation. The print preview option helps to view how the page will look after printing.
Question 6.
Mr. Franco’s e-mail id is [email protected]. He wants to connect this page fastly and he visited regularly. How can it possible?
Answer:
Mr. Franco regularly visited this site to visit this site he has to type the address repeatedly every time. It is laborious work and it can be avoided if he marks the particular address as favorite. A favorite is a link to a web page. So that he can access that page faster.
To do this click add to favorite option then a dialog box appears that asks for a name for the favorite. To make the web page available offline, then ‘Make available offline1 option has to be checked.
Question 7.
Match the following.
| (1) Browser | a. File |
| (2) Menu Bar | b. URL |
| (3) Tool Bar | c. Previous page |
| (4) Address Bar | d. Progress |
| (5) Status Bar | e. Mail icon |
| (6) Back Button | f. Mosaic |
Answer:
(1) f (2) a (3) e (4) b (5) d (6) c
Question 8.
Noby accessing internet by using a dial-up connection and manu using a direct connection. What is the difference between these two?
Answer:
There are two ways to connect to the internet. First one dialing to an ISP’s computer or with a direct connection to an ISP.
1. Dial-up Connection:
Here the internet connection is established by dialing into an ISP’s computer and they will connect our computer to the internet. It uses Serial Line Internet Protocol (SLIP) or Point to Point Protocol (PPP). It is slower and has a higher error rate.
2. Direct connection:
In direct connection there is a fixed cable or dedicated phone line to the ISP. Here it uses ISDN (Integrated Services Digital Network) a high speed version of a standard phone line. Another method is leased lines that uses fibre optic cables.
Digital Subscribers Line (DSL) is another direct connection, this uses copper wires instead of fibre optic for data transfer. Direct connection provides high speed internet connection and error rate is less.
Question 9.
Explain the different steps happened in between user’s click and the page being displayed.
Answer:
- The browser determines the URL selected.
- The browser asks the DNS for URLS corresponding IP address (Numeric address)
- The DNS returns the address to the browser.
- The browser makes a TCP connection using the IP address.
- Then it sends a GET request for the required file to the server.
- The server collects the file and send it back to the browser.
- The TCP connection is released.
- The text and the images in the web pages are displayed in the browser.
Question 10.
What is a Spamming?
Answer:
Sending an email without recipient’s consent to promote a product or service is called spamming. Such an email is called a spam.
Question 11.
You wish to visit the website of your school. Name the software required. Which software is available with Windows for this purpose? Give names of other such software.
Answer:
Browsing software or Browser. The browsers are:
- Netscape Navigator
- Internet Explorer
- Mozilla
- Opera
- Mosaic etc.
Question 12.
Suppose you want to collect information regarding Tsunami using Internet.
- Suggest a method for this purpose
- Explain one method adopted.
Answer:
A browser is a piece of software that acts as an interface between the user and the internal working of the internet. With the help of a browser the user can search information on the internet and it allows userto navigate through the web pages. The different browsers are
- Microsoft internet explorer
- Mozilla
- Netscape Navigator
- Mosaic
- Opera
Question 13.
What is a blog?
Answer:
Conducting discussions about particular subjects by entries or posts. The posts appeared in the reverse chronological order means the most recent post appears first.
eg: Blogger.com, WordPress.com, hsslive.com etc.
Question 14.
What do you mean by phishing.
Answer:
it is an attempt to get others information such as usenames, passwords, bank ale details etc by acting as the authorized website. Phishing websites have URLs and home pages similar to their original ones and mislead others, it is called spoofing.
Question 15.
What is quarantine?
Answer:
When you start an anti-virus program and if any fault found it stops the file from running and stores the file in a special area called Quarantine (isolated area) and can be deleted later.
Question 16.
Compare the intranet and extranet.
Answer:
A private network inside a company or organisation is called intranet and can be accessed by the company’s personnel. But Extranet allows vendors and business partners to access the company resources.
Question 17.
Write short notes on
- mobile broadband
- Wi-MAX
Answer:
- Mobile broadband: Accessing Internet using wireless devices like mobile phones, tablet, USB dongles, etc.
- Wi MAX(Wireless Microwave Access): It uses microwaves to transmit information across a network in a range 2GHz to 11GHz over very long distance.
Question 18.
Compare blogs and microblogs.
Answer:
Blogs: Conducting discussions about particular subjects by entries or posts. The posts appeared in the reverse chronological order means the most recent post appears first.
eg: Blogger.com, WordPress.com, hsslive.com etc.
Microblogs: It allows users to exchange short messages, multimedia files, etc.
eg: www.twitter.com
Question 19.
What is firewall?
Answer:
It is a system that controls the incoming and outgoing network traffic by analyzing the data and then provides security to the computer network in an organization from other networks (internet).
Question 20.
XYZ engineering college has advertised that its campus is Wi-Fi enabled. What is Wi-Fi? How is the Wi-Fi facility implemented in the campus.
Answer:
Wi-Fi means Wireless Fidelity. It is a wireless technology. Some organisation offers Wi-Fi facility. Here we can connect internet wirelessly over short distance, using Wi-Fi enabled devices.
It uses radio waves to transmit information across a network in a range 2.4 GHz to 5 GHz in short distance. Nowadays this technology is used to access internet in campuses, hypermarkets, hotels by using Laptops, Desktops, tablet, mobile phones etc.
Question 21.
What is GPS?
Answer:
It is a space based satellite navigation system that provides location and time information in all weather conditions, anywhere on or near the Earth where there is an unobstructed line of sight to four or more GPS satellites. The system provides critical capabilities to military, civil and commercial users around the world.
It is maintained by the United States government and is freely accessible to anyone with a GPS receiver. GPS was created and realized by the U.S. Department of Defense (DoD) and was originally run with 24 satellites. It is used for vehicle navigation, aircraft navigation, ship navigation, oil exploration, Fishing, etc. GPS receivers are now integrated with mobile phones.
Question 22.
Write short notes on SMS.
Answer:
Short Message Service(SMS):
It allows transferring short text messages containing up to 160 characters between mobile phones. The sent message reaches a Short Message Service Center(SMSC), that allows ‘store and forward’ systems. It uses the protocol SS7(Signaling System No7). The first SMS message ‘Merry Christmas’ was sent on 03/12/1992 from a PC to a mobile phone on the Vodafone GSM network in UK.
Question 23.
What is smart card? How it is useful?
Answer:
A smart card is a plastic card with a computer chip or memory that stores and transacts data. A smart card (may be like your ATM card) reader used to store and transmit data. The advantages are it is secure, intelligent and convenient. The smart card technology is used in SIM for GSM phones. A SIM card is used as an identification proof.
Question 24
Social media plays an important role in today’s life. Write notes supporting and opposing its impacts.(3)
Answer:
Advantages of social media:
- Bring people together: It allows people to maintain the friendship.
- Plan and organize events: It allows users to plan and organize events.
- Business promotion: It helps the firms to promote their sales.
- Social skills: There is a key role of the formation of society.
Disadvantages.
- Intrusion to privacy: Some people may misuse the personal information.
- Addiction: sometimes it may waste time and money.
- Spread rumours: The news will spread very quickly and negatively
Question 25.
One of your friends wants to send an email to his father abroad to convey him birthday wishes with a painting done by him. Explain the structure and working of email to him. (3)
Answer:
The email message contains the following fields.
- To: Recipient’s address will be enter here. Multiple recipients are also allowed by using coma.
- CC: Enter the address of other recipients to get a carbon copy of the message.
- bcc: The address to whom blind carbon copies are to be sent. This feature allows people to send copies to third recipient without the knowledge of primary and secondary recipients.
- From: Address of the sender
- Reply to: The email address to which replies are to be sent.
- Subject: Short summary of the message.
- Body: Here the actual message is to be typed.
Question 26.
Briefly explain any three mobile communication services.
Answer:
Mobile communication services.
1. Short Message Service(SMS):
It allows transferring short text messages containing up to 160 characters between mobile phones. The sent message reaches a Short Message Service Center(SMSC), that allows ‘store and forward’ systems. It uses the protocol SS7(Signaling System No7), The first SMS message ‘Merry Christmas’ was sent on 03/12/1992 from a PC to a mobile phone on the Vodafone GSM network in UK.
2. Multimedia Messaging Service (MMS):
It allows sending Multi-Media(text, picture, audio and video file) content using mobile phones. It is an extension of SMS.
3. Global Positioning System(GPS):
It is a space – based satellite navigation system that provides location and time information in all weather conditions, anywhere on or near the Earth where there is an unobstructed line of sight to four or more GPS satellites. The system provides critical capabilities to military, civil and commercial users around the world.
It is maintained by the United States government and is freely accessible to anyone with a GPS receiver. GPS was created and realized by the U.S. Department of Defense (DoD) and was originally run with 24 satellites. It is used for vehicle navigation, aircraft navigation, ship navigation, oil exploration, Fishing, etc. GPS receivers are now integrated with mobile phones.

4. Smart Cards:
A smart card is a plastic card with a computer chip or memory that stores and transacts data. A smart card (maybe like your ATM card) reader used to store and transmit data. The advantages are it is secure, intelligent and convenient. The smart card technology is used in SIM for GSM phones. A SIM card is used as an identification proof.
Question 27.
Define Internet. Compare two types of Internet connectivities namely Dial-up and Broadband.
Answer:
Types of connectivity
There are two ways to connect to the internet. First one dialing to an ISP’s computer or with a direct connection to an ISP.
Question 28.
1. your friend does not have an e-mail address. Suggest an e-mail address for him. Starting the advantages of e-mail, explain how it becomes useful for his further communications.
OR
2. List the possible risks while interacting with social media.
Answer:
1. An example of an email id isjobi_cg@rediffmail. com. here jobi_cg is the user name, rediffmail is the portal or website address and.com is the top level domain which identifies the type of organisation. Similarly, we can create an email id, for this type the URL “www.rediffmail.com” and for the new user you have to signup and create an email Id.
The advantages of email are given below:
- Speed is high
- It is cheap
- We can send email to multiple recipients.
- Incoming messages can be saved locally.
- It reduces the usage of paper.
- We can access mail box anytime and from any where.
2. The possible risks while interacting with social media is given below.
- Intrusion to privacy: Some people may mis use the personal information.
- Addiction: Sometimes due to addiction it may waste time and money.
- Spread rumours: The news will spread very quickly and negatively.
Question 29.
Mobile phone technology has evolved through four generations.
- Which generation is called Long Terms Evolution?
- Explain some major advancements evolved through these generations. (3)
Answer:
1. 4G
2. Generations in mobile communication
The mobile phone was introduced in the year 1946. Early stage it was expensive and limited services hence its growth was very slow. To solve this problem, cellular communication concept was developed in 1960’s at Bell Lab. 1990’s onwards cellular technology became a common standard in our country.
The various generations in mobile communication are:
(a) First Generation networks(1G):
It was developed around 1980, based on analog system and only voice transmission was allowed.
(b) Second Generation networks(2G):
This is the next generation network that was allowed voice and data transmission. Picture message and l\4MS(Multimedia Messaging Service) were introduced. GSM and CDMA standards were introduced by 2G.
(i) Global System for Mobile(GSM):
It is the most successful standard. It uses narrow band TDMA(Time Division Multiple Access), allows simultaneous calls on the same frequency range of 900 MHz to 1800 MHz. The network is identified using the SIM(Subscriber Identity Module).
(a) GPRS(General Packet Radio Services):
It is a packet oriented mobile data service on the 2G on GSM. GPRS was originally standardized by European Telecommunications Standards Institute (ETSI) GPRS usage is typically charged based on volume of data transferred. Usage above the bundle cap is either charged per megabyte or disallowed.
(b) EDGE(Enhanced Data rates for GSM Evolution):
It is three times faster than GPRS. It is used for voice communication as well as an internet connection.
(ii) Code Division Multiple Access(CDMA):
It is a channel access method used by various radio communication technologies. CDMA is an example of multiple access, which is where several transmitters can send information simultaneously over a single communication channel. This allows several users to share a band of frequencies To permit this to be achieved without undue interference between the users, and provide better security.
(c) Third Generation networks(3G):
It allows high data transfer rate for mobile devices and offers high speed wireless broadband services combining voice and data. To enjoy this service 3G enabled mobile towers and hand sets required.
(d) Fourth Generation networks(4G):
lt is also called Long Term Evolution(LTE) and also offers ultra broadband Internet facility such as high quality streaming video. It also offers good quality image and videos than TV.
Question 30.
What is browsing? Briefly explain the steps needed for browsing.
Answer:
The process of visiting a website is called browsing.
Web Browsing steps are given below:
- The browser determines the URL entered.
- The browser asks the DNS for URLS corresponding IP address (Numeric address)
- The DNS returns the address to the browser.
- The browser makes a TCP connection using the IP address.
- Then it sends a GET request for the required file to the server.
- The server collects the file and send it back to the browser.
- The TCP connection is released.
- The text and the images in the web pages are displayed in the browser.
Question 31.
Susheel’s email id is [email protected]. He sends an email to Rani whose email id is [email protected]. How is the mail sent from susheel’s computer to Rani’s computer?
Answer:
To send an email first type the recipients address and type the message then click the send button. The website’s server first check the email address is valid, if it is valid it will be sent otherwise the message will not be sent and the sender will get an email that it could not deliver the message.
This message will be received by the recipient’s server and will be delivered to recipient’s mail box. He can read it and it will remain in his mail box as long as he will be deleted. Simple Mail Transfer Protocol(SMTP) is used.
The advantages of email are given below:
- Speed is high
- It is cheap
- We can send email to multiple recipients
- Incoming messages can be saved locally
- It reduces the usage of paper
- We can access mail box anytime and from anywhere.
The disadvantages are:
- it requires a computer, a modem, software and internet connection to check mail.
- Some mails may contain viruses.
- Mail boxes are filled with junk mail. So very difficult to find the relevant mail.
Plus One Internet and Mobile Computing Five Mark Questions and Answers
Question 1.
Your younger brother does not know the structure of an email message. Explain the structure of an email message.
Answer:
The email message contains the following fields:
- To: Recipient’s address will be enter here. Multiple recipients are also allowed by using coma.
- CC: Enter the address of other recipients to get a carbon copy of the message.
- bcc: The address to whom blind carbon copies are to be sent. This feature allows people to send copies to third recipient without the knowledge of primary and secondary recipients.
- From: Address of the sender
- Reply to: The email address to which replies are to be sent.
- Subject: Short summary of the message.
- Body: Here the actual message is to be typed
Question 2.
‘Email is the most popular, but most misused service of the internet’. Justify your answer.
Answer:
The advantages of email are given below:
- Speed is high
- It is cheap
- We can send email to multiple recipients
- Incoming messages can be saved locally
- It reduces the usage of paper
- We can access mail box anytime and from anywhere.
The disadvantages are:
- it requires a computer, a modem, software and internet connection to check mail.
- Some mails may contain viruses
- Mail boxes are filled with junk mail. So very difficult to find the relevant mail
