Subject code CB3402 deals with the Operating Systems And Security subject. In this article, we try to provide the syllabus of the CB3402 Operating Systems And Security syllabus based on the Affiliated Institutions of Anna University 2021 Regulation syllabus.
If you see nowadays, students are requesting brief descriptions of anything they want to know. Today social media platforms and search engines are running information throughout the world, just by searching the concept by the people. Especially when it comes to education, every subject in any field has been provided. There is a lot of demand to provide accurate education information in the market. Among them is aplustopper.com tries to give the best of its content for students. In this article, the CB3402 – Operating Systems And Security Syllabus is given briefly without getting rid of a single concept of the subject from the Anna University B.E Computer Science and Engineering (Cyber security) syllabus.
If you want to know more about the syllabus of B.E Computer Science and Engineering (Cyber security) Syllabus connected to an affiliated institution’s four-year undergraduate degree program. We provide you with a detailed Year-wise, semester-wise, and Subject-wise syllabus in the following link B.E Computer Science and Engineering (Cyber security) Syllabus Anna University, Regulation 2021.
Aim Of Concept:
- To understand the basic concepts of Operating Systems.
- To explore the process management concepts including scheduling, synchronization, threads and deadlock.
- To understand the memory, file and I/O management activities of OS.
- To understand the requirements of a trust model.
- To learn how security is implemented in various operating systems.
CB3402 – Operating Systems And Security Syllabus
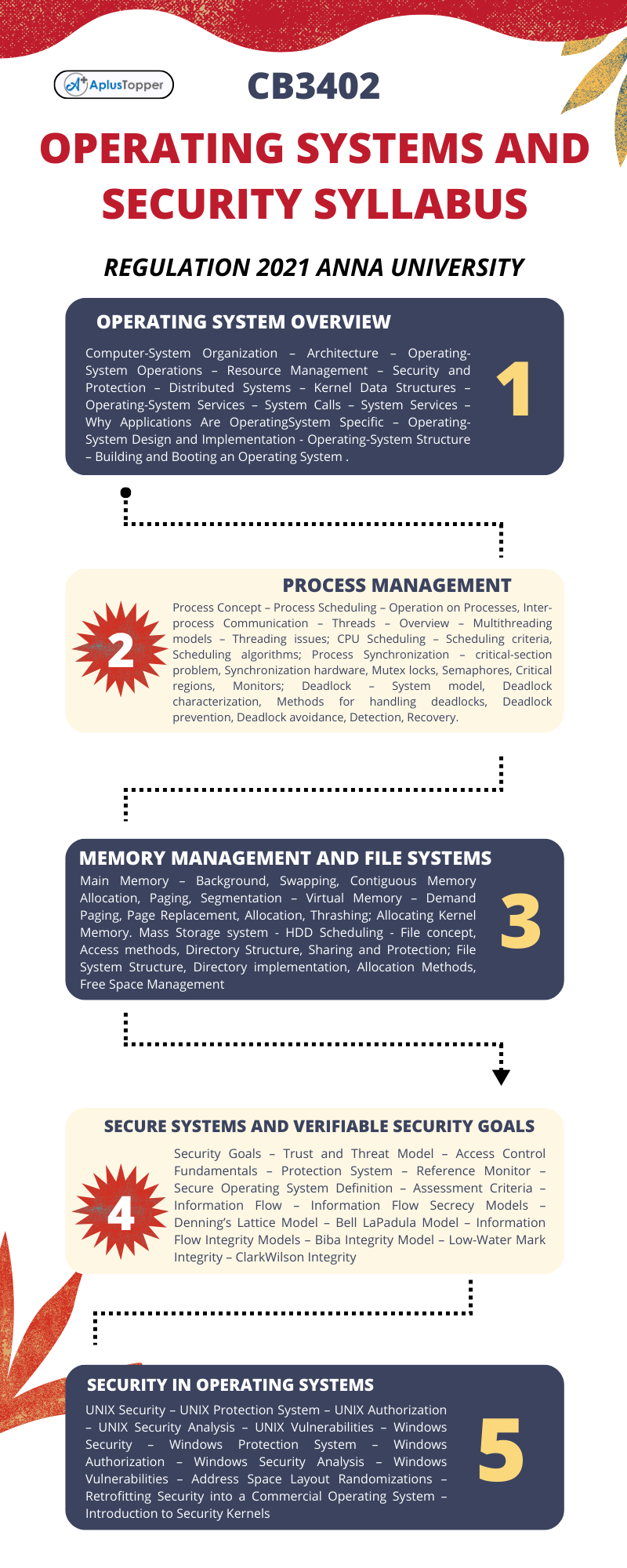
Unit I: Operating System Overview
Computer-System Organization – Architecture – Operating-System Operations – Resource Management – Security and Protection – Distributed Systems – Kernel Data Structures – Operating-System Services – System Calls – System Services – Why Applications Are OperatingSystem Specific – Operating-System Design and Implementation – Operating-System Structure – Building and Booting an Operating System .
Unit II: Process Management
Process Concept – Process Scheduling – Operation on Processes, Inter-process Communication – Threads – Overview – Multithreading models – Threading issues; CPU Scheduling – Scheduling criteria, Scheduling algorithms; Process Synchronization – critical-section problem, Synchronization hardware, Mutex locks, Semaphores, Critical regions, Monitors; Deadlock – System model, Deadlock characterization, Methods for handling deadlocks, Deadlock prevention, Deadlock avoidance, Detection, Recovery.
Unit III: Memory Management And File Systems
Main Memory – Background, Swapping, Contiguous Memory Allocation, Paging, Segmentation – Virtual Memory – Demand Paging, Page Replacement, Allocation, Thrashing; Allocating Kernel Memory. Mass Storage system – HDD Scheduling – File concept, Access methods, Directory Structure, Sharing and Protection; File System Structure, Directory implementation, Allocation Methods, Free Space Management
Unit IV: Secure Systems And Verifiable Security Goals
Security Goals – Trust and Threat Model – Access Control Fundamentals – Protection System – Reference Monitor – Secure Operating System Definition – Assessment Criteria – Information Flow – Information Flow Secrecy Models – Denning’s Lattice Model – Bell LaPadula Model – Information Flow Integrity Models – Biba Integrity Model – Low-Water Mark Integrity – ClarkWilson Integrity
Unit V: Security In Operating Systems
UNIX Security – UNIX Protection System – UNIX Authorization – UNIX Security Analysis – UNIX Vulnerabilities – Windows Security – Windows Protection System – Windows Authorization – Windows Security Analysis – Windows Vulnerabilities – Address Space Layout Randomizations – Retrofitting Security into a Commercial Operating System – Introduction to Security Kernels.
Practical Exercises:
- Basics of UNIX commands, Understand and practice Linux permissions, special permissions and authentication (various options of chmod, setuid, setgid)
- Write programs using the following system calls of UNIX operating system a. fork, exec, getpid, exit, wait, close, stat, opendir, readdir
- Write C programs to implement the various CPU Scheduling Algorithms
- Implementation of Semaphores
- Implementation of Shared memory
- Bankers Algorithm for Deadlock Detection &Avoidance
- Implementation of the following Memory Allocation Methods for fixed partition
a) First Fit b) Worst Fit c) Best Fit - Implementation of the following Page Replacement Algorithms
a) FIFO b) LRU c) LFU - Program to demonstrate the working of Bell LaPadula Model and Biba Integrity Model
- Setting up access control lists of files and directories and testing the lists in Linux
- Learn to enable and disable address space layout randomization
Text Book:
- Abraham Silberschatz, Peter Baer Galvin and Greg Gagne, “Operating System Concepts”, John Wiley & Sons, Inc., 10th Edition, 2021.
- Trent Jaeger, Operating System Security, Morgan & Claypool Publishers series, 2008.
References:
- Morrie Gasser, “Building A Secure Computer System”, Van Nostrand Reinhold, New York, 1988.
- Charles Pfleeger, Shari Pfleeger, Jonathan Margulies, “Security in Computing”, Fifth Edition, Prentice Hall, New Delhi, 2015.
- William Stallings, “Operating Systems – Internals and Design Principles”, 9th Edition, Pearson, 2017.
- Michael Palmer, “Guide to Operating Systems Security”, Course Technology – Cengage Learning, New Delhi, 2008.
Related Posts On Semester – IV:
- CS3452 – Theory of Computation
- CS3491 – Artificial Intelligence and Machine Learning
- CB3491 – Cryptography and Cyber Security
- GE3451 – Environmental Sciences and Sustainability
Must Read For More:
